January 13th, 2014

There are few experiences more frustrating than when you can’t connect to the internet or your connection is unbearably slow. Almost everything we do, whether for work or in our free time, requires an internet connection, which makes not having one painful. There are a few tools available to help you diagnose internet connectivity problems, but, as Alan Henry of LifeHacker reports, few are as simple and easy to use as the Connectivity Diagnostics app for Google’s Chrome web browser.
As frustrating as a lack of internet can be, perhaps even worse is not knowing what’s causing your outage. That’s why diagnostic apps like this one are so handy. Whether the issue is with your computer, router, network, or service provider, the Connectivity Diagnostics app finds it so you can fix it.
Unlike other similar applications, the Connectivity Diagnostics app doesn’t require any additional software installed to run. It works through Chrome and is completely free. To find the cause of your internet problems, it can check for an active connection, attempts to contact your DNS server, checks for firewalls blocking your connection or pay-portals, tests for DNS resolution delays and tests for network delays. Each test returns additional information on whether it was successful or not to help you pinpoint the problem.
This isn’t an enterprise level application, but it’s perfect for individual users. Because it’s simple to use, you don’t even need to be tech-savvy to diagnose your connectivity issues.
If your computer is having problems you can’t solve, call Geek Rescue at 918-369-4335.
January 2nd, 2014

Staying safe online requires the right security tools. It also requires the right knowledge of common threats. Knowing how criminals typically attack your computer educates you on how to prevent those attacks. Roger A. Grimes at Computer World published his list of the most devious attacks currently being used and how to protect yourself from them.
There a plenty of public places where people typically use free, public WiFi. Unfortunately, networks in places like coffee shops, libraries and airports are also common targets for hackers. They’re able to set-up fake wireless access points, or WAPs, that fool users. Users connect using a network with a believable name, but are actually giving a criminal access to all the data they transmit. This is an easy way for hackers to steal passwords, banking information and more. To protect yourself, be extremely wary of public WiFi. Don’t enter any financial information or visit any sites that require a password.
Cookies have been used by websites for years to make your browsing experience faster and more convenient. These text files store information so you don’t have to log-in every time you visit the same site, or otherwise streamline your experience. That information is dangerous if stolen, however. Hackers use a number of methods for stealing cookies. When they’re successful, they’re able to immediately gain access to certain sites and sometimes even gain payment information. Make sure that if you have cookies enabled, you’re only using HTTPS websites that use the latest encryption methods.
This is not only a common attack method, but also a simple one. Hackers use some social engineering to gain more downloads of malicious files and tempt more users to open those files. No one would want to download ‘malware.exe’, but when the file name is something more salacious or relevant to the user, many can’t resist. Some even use false file extensions to confuse users. The full file name may be ‘image.jpeg.exe’. The file is an executable application, not an image, but ‘.jpeg’ fools many users. To protect yourself, don’t download files that sound too good to be true and only download from trusted sources. If you aren’t expecting a file to be emailed to you, don’t open any attachments. Also, be sure to scan anything you download with your antivirus program before you open it.
Windows users have a DNS-related file named ‘Hosts’ in their ‘Drivers’ folder. Typically, there’s no reason for a normal user to interact with ‘Hosts’. It contains domain names that a user has visited and links them to their IP addresses. This is a way around having to contact DNS servers and perform recursive name resolution every time a popular site is visited. But, this opens the door for hackers to enter their own malicious entries into ‘Hosts’. By changing the IP addresses linked to common domain names, a hacker can redirect users to a spoofed version of a legitimate site. These malicious sites usually look very similar to the original, but are used to steal your data. This is a difficult attack to spot. If a site looks different than usual, avoid it. Don’t enter any information on a site that looks different than you’d expect. If you suspect you’re being maliciously redirected, examine your ‘Hosts’ file.
These are only a small collection of ways criminals can steal your data and infect your computer. For help improving your security, or fixing the effects an attack has had on your system, call Geek Rescue at 918-369-4335.
December 20th, 2013

The update for Windows 8 has been available for about three months. Some of the new features are obvious, like the re-inclusion of the ‘Start’ button. But, as Ciprian Rusen of LifeHacker writes, there are a few interesting features that aren’t so evident. Not all of these are changes for the better, but all affect the way you’ll use Windows 8.1.
One of the biggest advances within Windows 8.1 is the ability to block the data apps from the Windows Store have access to. You can prevent apps from accessing your name and location. You can also turn off the advertising ID so you don’t get personalized ads using your information. Best of all, you can limit what apps have access to your microphone and webcam.
A virtual private network, or VPN, is a powerful tool for keeping your data safe when surfing the web. It’s particularly useful when you’d otherwise be on an unsecured connection like public WiFi. Windows 8.1 offers better support for VPNs than any previous version of the operating system. There are a number of new customization options when setting up your VPN and even included support for certain providers. Windows will even prompt you to sign into your VPN when an app attempts to access information best accessed over a secure connection.
Part of the updates included with the jump to Windows 8.1 was an update to Internet Explorer that introduces Reading Mode. Load any page with IE 11 and you’ll have a Reading Mode icon in the address bar. Using it will reload the page without distracting elements like ads to allow you to easily read the content you came for.
- No Right-Click From Networks List
In Windows 8, users could right click on a Network and access customization options for that network connection or even use the ‘Forget Network’ option to remove the connection for the list. In Windows 8.1, this capability has been removed. Customization options for network connections haven’t been removed, they’re just more difficult to access.
- SkyDrive Unavailable Offline
SkyDrive and Windows 8.1 have already had their problems, as reported by many users. A planned change with this update was to make SkyDrive documents only available with an internet connection. Files aren’t fully downloaded to your hard drive, so you’re only able to access them from the cloud with an active internet connection. A new column in the SkyDrive folder, called ‘Availability’, tells you if a file is ‘Available offline’ or ‘Online only’. This change is intended to help tablet users and those with very little available hard drive space. For those with more available space that want to avoid this irritation, changing the default to allow all files to be accessible while offline is easy to do through the ‘Settings’ menu.
Whether you’re running the latest version of Windows on a new PC or using an older computer, Geek Rescue has you covered for repairs. Whatever the problem you’re having is, call us at 918-369-4335 and we’ll fix it.
December 19th, 2013

If you’re on the ball this holiday season, you’ve probably already completed your online holiday shopping. For those who like to wait until the last minute, there’s still time with expedited shipping to find the perfect gift online. When you do shop online, it’s important to know how to stay protected to avoid scams, malware and identity theft. A post on the 2-Spyware blog details some of the threats to your security and what you’ll need to avoid them when shopping online.
Before you start surfing the web, check to make sure your antivirus program is up to date. You need to update your antivirus often because new malware is introduced every day and updating helps your antivirus identify and protect you from those latest threats. When shopping online, you’re more likely to visit sites you are unfamiliar with while searching for a deal. That makes it more likely you’ll visit a malicious site that’s designed to infect your computer with malware. Ecommerce sites also naturally experience more traffic during the holiday shopping season, which makes them more attractive targets for hackers than other times. This means that even trusted sites may be compromised.
If you’re shopping at sites you haven’t used before, you’ll probably be asked to create an account. It’s important to use a strong password that is long and uses upper and lower case letters, numbers and symbols so it’s difficult to hack. It’s also important not to use the same password for each account you create. Some of these sites may have less security than others, which means if their passwords are stolen and you use identical passwords for multiple sites, a hacker could gain access to all of your accounts.
Where you do your holiday shopping is also important. If shopping from home, make sure your network is secured and you’re using a firewall. Shopping while out and about it tempting, but it isn’t recommended. Public WiFi doesn’t offer any type of security. So, anytime you enter your account log-in and credit card information, that data can be monitored and stolen by a third party.
There are major sites like Amazon that you can trust to keep your payment information secure, but holiday shopping can sometimes lead you to untrusted sites in search of a deal. Some of these sites are completely legitimate, but don’t do enough to keep your information from being stolen. Other sites are scams claiming to sell popular items, but in reality they’re designed to steal your credit card information or infect your computer with malware.
Online shopping is convenient and a great way to quickly finish buying gifts, but it can also lead to costly cyber attacks.
For help improving the security on your computer or network, call Geek Rescue at 918-369-4355.
December 2nd, 2013

Cyber Monday marks the beginning of a busy online shopping season. Unfortunately, that’s well known information, which means criminals will be targeting shoppers hoping to cash in on the holiday season. To keep yourself, and your bank account, safe, Jennifer LeClaire of Lumension suggests doing your online shopping and banking on a mobile device.
Many users assume that a mobile device, like a tablet or smartphone, is less secure than their PC. This is usually only true because they’ve failed to take the same security precautions on their mobile device that they have on their laptop or desktop. With security apps in place, mobile devices can be much more secure because there are far fewer threats specifically targeting them.
There are certainly pieces of malware made specifically for Android, and to a lesser extent Apple’s iOS, but it pales in comparison to the threats being produced for PCs. Both Apple and Android provide security in their app store. As long as users don’t venture outside of the store to download unverified apps, they should have an entirely safe environment. PC users typically download more and take more risks online, which leaves their PC teeming with vulnerabilities and possible infections.
If your mobile device has an antivirus app installed, and is absent of any existing malware, you’ll have a great foundation for a secure online shopping season. You’ll still want to use smart surfing tactics, however. For example, don’t use public WiFi for any activity where you’re asked to log-in to an account, or provide payment information. Public WiFi provides no security for your data, which allows criminals to easily intercept any information you send over that network. So, while a mobile device may be more secure for online shopping than your PC, it shouldn’t be used just anywhere. Shop from home on your own, secured network.
Regardless of how you plan to do your online shopping this year, you need to take the proper precautions. To secure any of your devices, remove viruses and malware, or to create a more secure network at home or the office, call Geek Rescue at 918-369-4335.
December 2nd, 2013

When you visit your bank’s website, most retailers or a credit card’s website, you might notice that the address starts with “HTTPS”. The added ‘S’ stands for secure. That’s ‘Hypertext Transfer Protocol Secure’ all together. It denotes that the site you’re using is safe from hackers stealing your log-in information. While that may have been true at one time, Rohit Sethi writes for USA Today that HTTPS alone no longer provides complete security for users.
HTTPS remains a useful tool to keep users secure, but it can’t do the job alone. Hackers have already exposed some areas of weakness. In another two to five years, successful attacks on HTTPS could become so common that an entirely new structure will be needed.
When using a site with HTTPS, your data is encrypted so that no third party will be able to steal it. However, attacks have already taken place that allow hackers to bypass this security. This means that log-in information for important online accounts, like for banking sites, is easily stolen by criminals in less than a minute. For both websites and users, this poses a particular problem because both parties believe in the security HTTPS is supposed to provide.
Users must understand that an HTTPS included in a URL and a small lock icon no longer provides enough security. Fortunately, there are other ways to keep your data safe. A Virtual Private Network, VPN, is one valuable tool. It provides an extra layer of encryption for all of your browsing activity. Many VPNs contain the same type of security flaws that have been exploited in HTTPS, so do some research and find a VPN using IPsec.
Smart, safe surfing habits also go a long way in protecting your data. Unsecured wireless networks provide little security, so if you’re using one, don’t log-in to any of your online accounts. Also, consider having a credit card dedicated to online purchases. This way, if that card is compromised, a criminal won’t have access to your entire bank account and you should notice quickly.
If you’d like to improve security for any device at home or at the office, or if you need to upgrade security for your website, call Geek Rescue for help at 918-369-4335.
November 29th, 2013

There are a number of precautions you need to take in order to stay safe online. From firewalls to updated antivirus software, there are plenty of tools that can prevent a disastrous cyber attack or data breach. These tools still don’t guarantee your safety, however. Even with precautions in place, it’s important to understand where the majority of threats come from and avoid them altogether with safe surfing techniques. Ron Johnson, of Business2Community, listed some of the most common causes of security breaches and how to avoid them.
Open WiFi networks are found nearly everywhere you go, but they’re far from secure. Any data you send over public WiFi is easily intercepted and stolen by a third party. This doesn’t mean you shouldn’t ever connect to public WiFi. It means you need to be extra careful about what sites you access while using this type of unsecured network. Viewing and reading websites likely won’t cause a problem, but don’t log-in to any online accounts or your password could be compromised.
Most users understand the dangers in giving other people their password, but sometimes even the most savvy users give out their log-in information without even thinking about it. For example, if you’re having difficulty with an account, a customer service representative might ask you for your password. This doesn’t necessarily mean they are going to misuse it, but it’s always a good idea to change passwords once you’ve told them to anyone, including a help desk. They might not always be as careful with your information as you would be. It’s also never a good idea to share accounts with others, even friends or family. If you want to allow another individual to access your account, change the password, give them the new log-in information, then change it again once they’re finished.
Downloading anything should be a decision that every user is cautious of. Even seemingly trusted websites can be compromised and a file you download could end up infecting your system with malware. If you’re prompted to download an application, like a media player, go to that player’s official website to download. Be sure to scan every file downloaded with your antivirus program before opening. As for email attachments, don’t download them unless you were expecting a file to be sent to you and you know exactly what it is.
Speaking of email, phishing scams are a popular method for stealing your information and hacking into your online accounts. These scams have grown more sophisticated. Often, an email will appear to be from a legitimate website where you hold an account. It will claim there’s been a problem and you need to log-in immediately, or download software, or even put in credit card information. If you have any questions about the legitimacy of these emails, contact the website or business directly, by phone if possible. There’s never a time when a business will email and need your credit card information.
By learning some of these common hacker tactics, you’ll be able to be smarter about your online habits and avoid potential threats.
If you’d like to improve security at your home or business to further safeguard from malware, phishing scams, hacking and more, contact Geek Rescue at 918-369-4335.
November 26th, 2013

Wireless internet can be finicky. You may get a strong signal in parts of your house, but a weak signal in some rooms. You may also notice your connection seems to get slower over time, or you experience disconnects frequently. As Steven Scheck writes for Business2Community, there are fixes to these common WiFi problems. Here are some ways to improve your wireless internet experience.
There’s not much expertise needed to optimize your wireless internet connection, but some basic knowledge is helpful. For example, your router uses a channel, similar to a radio signal, to broadcast. If you are using the same channel as another router close by, it could cause interference. If you’re experience problems with your WiFi, such as a slow connection, try changing the channel in the router’s settings. Also, if you’re using a ‘g’ or ‘b’ router, it’s time to upgrade. These are typically older models with limited capabilities. Instead, upgrade to a ‘N’ router and you will see dramatically improved performance, such as a larger range and more reliable connection.
The physical location of your router has a significant impact on the quality of your connection. Each router has a limited range, so the closer you are to the router, the more likely you are to enjoy a strong connection. So, place the router in a central location in your home. Also, try to keep it away from devices that would cause interference, such as other routers, or even microwaves. Keep in mind when placing your router that signals are weakened when they pass through furniture and walls.
If you’re out of options and your wireless network still doesn’t provide a strong connection throughout your home, it’s time for WiFi Repeater. By placing Repeater in range of your router, you’ll enjoy a stronger signal from farther from your router’s physical location. The range of your router will be up to twice as large.
Being able to connect to the internet isn’t the only mark of a successful wireless network. Be sure you have the proper security in place. To do so, make sure you’ve changed the log-in information from the factory settings. Turn on encryption and MAC address filtering. Change the default SSID and disable SSID broadcasts. It’s also important to put a firewall in place for your router and PC.
These tips help you create a quality wireless network in your home. For help with your network, to improve security, or to fix broken or malfunctioning hardware, call Geek Rescue at 918-369-4335.
November 18th, 2013

At this point, your phone is probably your most prized possession. You probably even feel strange if it isn’t with you. You can use your smartphone for almost anything, which means that the battery doesn’t last as long as you’d like. Jennifer Jolly, of USA Today, has some tips for how to get the most battery life out of your smartphone. These tips don’t even require you to sacrifice performance.
- Get Rid Of The Unwanted Features
Many of us don’t use our phone with bluetooth. You might not be in range of WiFi or in need of GPS services. There are features on your phone that you either never use, or only use in certain situations. If you need to get more life out of your smartphone’s battery, turn these services off until you want to use them.
Your smartphone’s display drains more battery than anything else. Turning down your brightness settings can have a significant impact on your battery. In most settings, even the lowest brightness setting is easy to see and you’ll get a much longer battery life out of it.
Many users leave their smartphones on vibrate all of the time. That saves you from being the annoying person whose ringtone goes off in a meeting, but it drains your battery. Yes, it takes more battery to vibrate than it does to ring. If you’re desperate for more battery life, you’ll have to live with your ringtone.
Free apps are riddled with advertisements. It takes battery power to download and display those advertisements. So, pay the money for the full version that’s ad free and you’ll get a slight uptick in battery life. This is only helpful for apps you use often. Otherwise, you probably won’t see enough extra battery life to warrant the payment.
Keeping apps updated is also helpful for lowering battery life because many updates make apps more efficient. But, allowing your phone to auto-update is wasteful to the battery. This is because your phone is constantly checking to see if an update is available. Instead, just try to remember to check for updates on your own when it’s convenient.
With these tips, you can keep your phone from dying in the middle of the day.
If you have problems more severe than a dying battery, call Geek Rescue at 918-369-4335. We fix all brands of smartphones.
November 15th, 2013
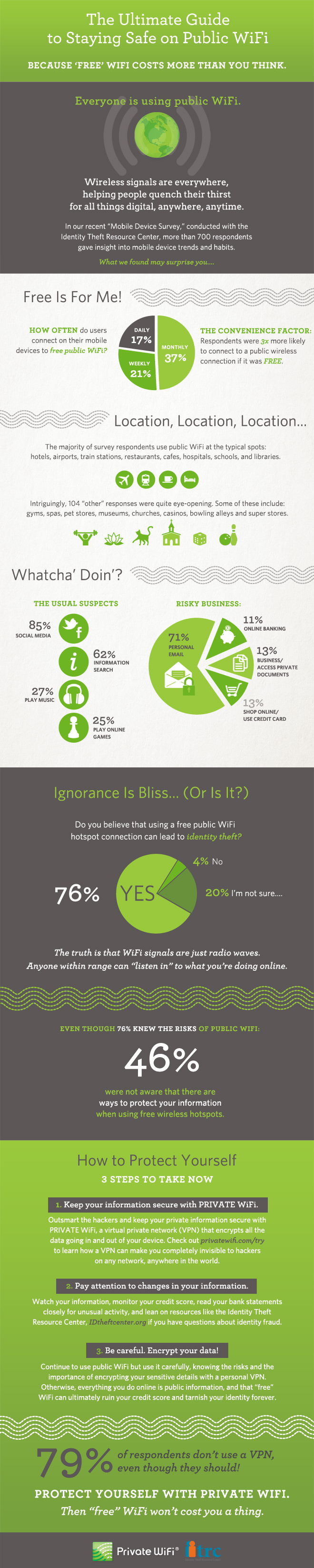
Free, public WiFi is offered nearly everywhere. Whether you’re at a library, coffee shop, restaurant, hotel, airport or hospital, you’ll be able to stay connected. That free WiFi comes with some inherent risks, however. PrivateWiFi and the Identity Theft Resource Center teamed up to produce this infographic, which details the general feelings about free WiFi and how you can stay secure while using it.
More than three-quarters of users understand that public WiFi isn’t secure. That’s the first step in a safer experience because those users will know not to log-in to their personal email or banking site while using an unsecured network. These safe surfing tactics aren’t the only way to improve security, however.
If a public network is unsafe, then why not use a private network? Even when connected to public WiFi, you can use a VPN to immediately improve security. There are a number of VPNs available. While many require a paid subscription, some are free up to a certain point. The VPN encrypts data being sent by your device and the data being returned to it.
A good idea is to keep close tabs on your online accounts, your financial information and your credit score regardless of the kind of network you’ve been using. But, it’s especially important to monitor your information if you know you’ve been on a public network. You probably won’t know immediately if someone hacks into your bank account or steals your identity. Regularly checking this information will save you from devastating damage because you’ll be able to recognize the first signs of trouble.
Understanding what’s at stake and when your information is most vulnerable is an effective way to stay more secure. When using free WiFi, try to avoid any site that require you to log-in. If you absolutely must log-in over an unsecured network, look into putting a VPN in place before doing so.
With more and more free wireless networks available, it’s more important to learn how to safely use them.
For more help improving the security of any of your devices at home or at the office, call Geek Rescue at 918-369-4335.




















