November 11th, 2013

Software companies like Microsoft, Apple and Adobe release patches regularly to fix bugs and close security vulnerabilities. This is a common practice, but as Tyler Reguly of TripWire’s State of Security blog reports, Microsoft often makes a mess of it.
There are a number of factors that contribute to the confusing nature of Microsoft’s patch practices. Patch Tuesday occurs once a month and involves the patching of multiple Microsoft products and fix multiple vulnerabilities at a time. The downside to this bulk patch release is that new vulnerabilities that crop up are left open for weeks while users wait for the next Patch Tuesday to come around. There have been instances in the past when Microsoft has pushed out a patch outside of this schedule and other companies follow a similar patching process, but users are still left in the lurch from time to time.
In addition, patches are far from uniform. Microsoft could release multiple patches to fix a single vulnerability in a single product, or they could release one patch per product for each instance of a vulnerability. Some patches replace older patches, but sometimes multiple patches are needed to replace a single patch.
In an attempt to simplify this process, Microsoft introduced a single service that would automatically update Windows users with any applicable patches for all Microsoft products in use on their device. This actually caused more confusion, however. A user who has enabled automatic updates might think they’re fully patched at all times, but that’s rarely the case. That’s usually because an older version of an application is being used that Microsoft no longer supports or that won’t work with automatic updates.
Unfortunately, users aren’t warned that applications aren’t being updated. Instead, it appears they’re patched and safe from vulnerabilities. In many ways, this makes them more susceptible to breaches than if they knowingly avoided all patches to begin with.
Keeping your devices and networks safe requires an investment. Geek Rescue offers help for improving security for your home or business. Call us at 918-369-4335.
November 7th, 2013

What do you know about threat feeds? These are a real time warning system that allow security teams to take necessary precautions to prevent the latest threats. They can be an incredibly useful resource for protecting your business. As Eric Ogren, of Computer World, points out, however, you may not have the necessary resources to adequately use threat feed. Instead, they might be best left to a third party vendor who handles your security.
- Find Threats Specific To Your Business
A threat feed isn’t tailored to you specifically. Instead, it’s a broad view of the latest threats in the wild. So, part of the investment involves combing through these feeds with a knowledge of your IT infrastructure and being able to recognize the threats that pose the biggest danger to you. This takes time and a high level of expertise. If you have both of these, a threat feed can serve you well. If you don’t, you’ll probably be better served letting a third party handle it.
- Developing Your Own Protection
Once you’ve discovered threats that are dangerous to you, you’ll want to protect against them. That means developing your own anti-malware signatures and patching your own security. These are the same types of actions an antivirus program would take, but you’ll be able to roll them out faster. That is, if you have the resources and knowledge available.
- Do You Have The Resources?
As mentioned, threat feeds present an opportunity to stay ahead of cyber attacks by recognizing the latest threats to your business. You have to have the capabilities to not only identify these threats, however, but also to take action to prevent them. If your team is capable, threat feeds should become a staple of your security.
If you’d like to leave your company’s security in the hands of the professionals, call Geek Rescue at 918-369-4335. We’re equipped to protect you against the latest threats and keep your data secure.
November 7th, 2013

There are many reasons to protect against cyber attacks. You need to protect your data, and your customer’s information, from third party criminals. You also want to avoid downtime, which prevents your customers from accessing your services or your employees from working. There are many issues involved in the fallout of a cyber attack, but the most telling is the monetary cost to your business. Jesmond Darminin, of IT News, reports that the cost associated with cyber attacks has grown for the fourth consecutive year. In addition to the costs, the frequency of attacks and the time it takes to resolve them are also on the rise.
The Ponemon Institute conducted their initial Cost of Cyber Crime Study four years ago. Since then, the cost has increased by 78-percent to an annual cost of more than $11.5 million on average, per company. In the past year alone, the average cost increased 26-percent, or $2.6-million more per attack. The companies involved in the study reported a range of costs between $1.3-million to $58-million. The average cost to overcome a single attack has reached $1-million.
During the same four-year time span, the amount of time it takes to overcome a cyber attack has also increased significantly. It takes nearly 130-percent longer to resolve a cyber attack now than it did in 2009. Companies reported it took an average of 32 days to resolve an attack. During this time, companies suffered a loss of about $33-thousand per day.
These increases can be attributed to more intelligent, sophisticated cyber attacks. More attention to security is needed than ever before and when an attacker finds a vulnerability, they’re able to do more damage and remain undetected for longer.
Companies suffered an average of 122 successful attacks per week, which is skewed by larger enterprises, but still illustrates the severity of the situation. Even though smaller businesses will likely experience fewer cyber attack attempts, once they become successful, they’ll likely begin to experience more.
That’s why a robust and effective security infrastructure is vital for your business. For help keeping your company safe, or for help recovering from a successful attack, call Geek Rescue at 918-369-4335.
November 5th, 2013

We’ve mentioned before that you can’t ever be completely secure online. But, some actions you take make you more secure and significantly less likely to be hacked. Andy O’Donnell of About suggests a number of mistakes that are commonly made and how they can lead to hacking. Here’s a list of some of the most common, as well as how you can avoid making them.
- Not Using Unique Passwords
Why would you need more than one password for your online accounts? If you use a long, strong password that’s difficult to break, you should be safe, right? Actually, no. Not all accounts are compromised by a third party guessing or breaking your password. Sometimes, large lists of passwords are stolen from companies. If your password is the same on every site you have an account with, a criminal could now have access to all those sites, rather than just the one. If you’re worried about remembering all of those unique passwords, consider using a password manager.
- Using An Unsecured Wireless Network
Whether it’s at home or at the office, your wireless network needs to be secured to keep out intruders. First, make sure you’re using adequate encryption. Check your router’s settings and enable WPA2 based encryption, rather than the less secure WEP. Then, set a long, strong password using upper and lowercase letters, symbols and numbers. Try to avoid using things like pets’ or children’s names or birth dates because those are likely to be known, or able to be found out, by others.
If you receive an unsolicited email with an attachment, don’t download the attachment. It’s simple advice, but many users believe they can download the attachment to find out what it is. In actuality, they’re downloading malware, which immediately infects their system. The same goes with pop-ups. Even with a pop-up blocker active in your web browser, you may see pop-ups from time to time, especially if you’re on a questionable website. Clicking on these pop-ups will often start a malware download.
To be properly secured, you need an active antivirus program and a firewall in place. These have to be turned on to work. This seems obvious, but many users will disable them if their computer is running slow, or if they’re having trouble running another application. This is ill advised. Also, security software needs to be continuously updated. This is to enable to software to recognize the latest pieces of malware and viruses. If you fail to update your antivirus, it becomes less and less effective.
These common mistakes make you an attractive target for hackers. To improve your cyber security, or to fix the damage already done to a device by malware and viruses, call Geek Rescue at 918-369-4335.
November 4th, 2013
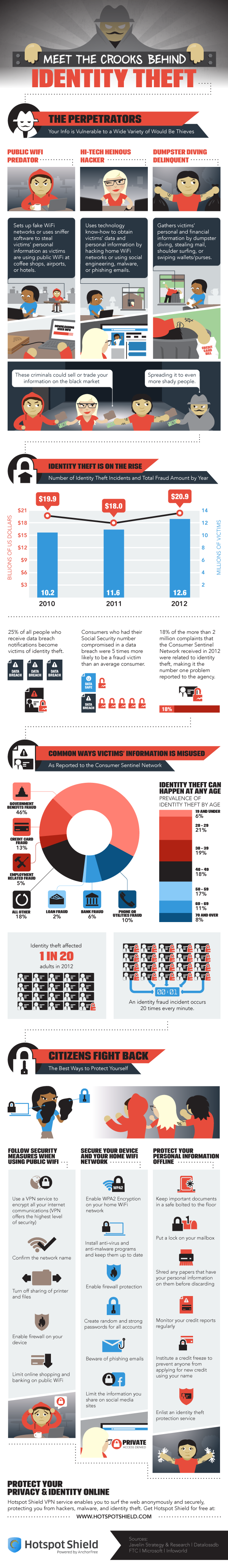
Protecting your computer from viruses and malware is only part of the concern of cyber security. Identity theft, which often begins with data being stolen over unsecure networks, through malware, or phishing scams, is also a costly threat.
Peter Nguyen, of the HotSpot Shield blog, writes that the number of identity thefts in the US is constantly growing. Last year, there were 12.6-million victims, which is enough for an identity theft to happen every 3-seconds. The financial loss of the victims totaled almost $21-billion.
The included infographic covers the how and why of identity theft. It also gives a few tips for how to stay safe. In addition to some offline measures, like shredding documents containing personal information, monitoring your credit reports, and locking your mailbox, here are the most important online safety tips.
- Beware public WiFi. When using an unsecured network at a coffee shop or other public place, limit your activity. Any transactions that require you to input financial information should wait. A firewall should be enabled on your device and you should turn off sharing of printers and files.
- Use proper security on your home wireless router. The router is your first line of defense, so make sure WPA2 encryption is enabled and a strong password is required to log on.
- Keep antivirus programs running in the background and keep them updated. Updating security software enables them to detect and protect against the latest threats.
- Keep social media profiles private. Every social network gives you options for what you share with whom. Make sure strangers don’t have access to information like your birthday, family information, phone number and employment history. This can all be used for identity fraud.
- Use long, strong passwords. Many security experts suggest passwords longer than 6-characters and using both upper and lowercase letters, numbers and symbols.
To improve the security of your devices at home, or at your business, call Geek Rescue at 918-369-4335. We not only fix devices, we also help keep them safe.
October 21st, 2013

As we’ve mentioned before, it’s impossible to be completely secure. Hackers continually adjust their tactics and upgrade their tools to breach any network. Because of this constant evolution, security has to constantly change and be updated as well. Your security infrastructure becomes less effective every day. Debbie Mahler, of the State of Security blog, writes that security is a process. She suggests some tips for how to continually improve your cyber security.
- Identify the weakest link
In order to improve security, you first have to find out where it needs to be improved. Usually, employees are the downfall of any security infrastructure. Unsafe web surfing habits, or human error often result in breaches. It’s important to study their habits in order to put policies in place that will keep your business more secure.
Having a firewall in place, and password protection on routers is a great step towards being more secure. But, too many people fail to utilize the tools they have at their disposal. For example, there have been many instances of security breaches stemming from a failure to change default passwords on routers. If you’ve taken the time to put these measures in place, take the additional time to make sure you’re using them effectively.
This is a common IT security rule. For any file, no one should have access. That’s where you start, then add permissions as necessary. This will keep your most valuable data secure because only a select few will have access to it.
Catastrophic data breaches usually happen after your network has been infiltrated previously. And, each time there’s suspicious behavior on your network, the logs have the evidence. Be sure to regularly review the logs in order to catch potentially harmful situations before they explode into disasters.
Security for your business is a big job that requires constant supervision. For help, contact Geek Rescue at 918-369-4335. We offer security audits and solutions for any breaches in your current security infrastructure.
October 21st, 2013

The security of data is extremely important for any business. The loss of data by any means can mean you’re unable to do business, or you’ve put your customers at risk. Sharon Florentine, of CIO, has a list of some common security risks and how to deal with them.
Smartphones are constantly being left behind in airports, coffee shops and bars. Laptops and tablets are the prime targets for thieves. When these devices have access to vital company data, or store data themselves, it becomes a serious problem. To combat it, back-up everything so you’ll still have access to it when that device disappears. Also, be sure to put protection in place so you can remotely wipe the device of any potentially harmful information.
Bring Your Own Device refers to employees using personal devices to access the company network and company files. This becomes a security headache because most individual’s fail to put proper security in place on their devices, and the devices might be infected with malware, which can then infect the entire network. Limiting employee access to certain files when on their own device is important. Ensuring that each employee has proper security in place on their devices is as well.
Without the proper protection in place, traffic from your network, or to your website, could be redirected through someone else’s server. This would allow that third party to collect data. For your most vital files and applications, create lists of authorized users, devices and IP addresses so no one else is able to access them.
There are unfortunately a number of ways to lose valuable data. Whether a device is physically stolen, or digitally compromised, you need to plan ahead for disaster.
Geek Rescue has the tools to help secure your company data, and recover and restore lost data. Call us at 918-369-4335 to improve your company’s cyber security.
October 21st, 2013

A lot of attention has been paid to Google’s recent changes. From their Hummingbird update of their search algorithm, and encrypting searches, there’s been no shortage of headlines about the search giant’s actions. Their latest move, however, isn’t about improving their own site. Instead, it’s an attempt to improve security for smaller, at risk sites.
Lorenzo Franceschi-Bicchierai, of Mashable, reports that Google has launched ‘Project Shield’, which allows small websites to offer content through Google’s infrastructure to keep them from being taken down by Distributed Denial of Service attacks.
A DDoS attack is a cyber attack that attempts to shut down a website by overloading it with malicious traffic. The traffic is impossible to block because it originates from thousands of individual, compromised machines.
With Project Shield, Google is trying to help individually owned websites that serve a public good in so-called “high risk conflict zones”. These would include Syria, Egypt and any country where the internet is controlled by the government.
In such countries, governments have used DDoS attacks in the past to take down certain websites. One example of this is a Syrian website set up by an activist to track scud missiles. The Syrian government used a DDoS attack to knock the site offline in July.
With it’s own DDoS prevention measures and an offering to serve content through Google’s resources, Project Shield is hoping to protect these types of sites, which are usually operated by small human rights organizations without the means to protect themselves.
Google is currently accepting applications to be “trusted testers” from sites that feel they deserve Project Shield’s protection.
For businesses in the US, Google is not offering such protection, but DDoS attacks and other cyber threats remain a serious concern. To improve your company’s security, contact Geek Rescue. We offer a variety of security solutions to keep you safe from attacks. Call us at 918-369-4335.
October 10th, 2013

Phishing scams are attempts to trick users to give out personal information so hackers can then use it to break into accounts and steal their identities. Most phishing scams start with an email that directs users to a website where they’er asked for information like their phone number, physical address and even social security number or banking information. There are a number of tell-tale signs of a phishing email, which makes many people believe they could never fall for one. As Sam Narisi of IT Manager Daily reports, a recent study by the Polytechnic Institute of New York suggests otherwise.
The study consisted of 100 science and engineering students. The students were given a personality test and asked about their computer use and proficiency. The researchers then anonymously sent a phishing scam to their personal accounts. The email included the usual signs of a scam, including misspellings and other errors. Still, 17 students fell for it and willingly gave out personal information.
What this study uncovers is that everyone is at risk to become a victim of a phishing scam. Due to social engineering when developing these scams, and a carelessness by users, even the most educated individual could still be a victim.
This extends to other threats, like malware, that infect your system through careless user actions. When a user isn’t extremely cautious online, bad things happen. This is costly for users on their personal computers at home, but it’s a huge risk for businesses who have to safeguard their entire network from numerous careless users.
Education is a great place to start to protect yourself and your office. Knowing what to look for in a potential cyber threat is important, despite the results of the study. Additional security measures also need to be put in place, however, with the knowledge that, eventually, someone is going to click on the wrong link.
To improve the security on any of your devices, at home or at the office, contact Geek Rescue at 918-369-4335.
October 7th, 2013

It seems like everyday there’s a new story about a major company or website that’s been hacked or attacked by malware. Many times, as Steve Johnson of the San Jose Mercury News reports, these attacks stem from initial infections that slip past security software and remain undetected for days, weeks or even months.
The New York Times recently encountered 45 pieces of malware that had remained on their computers for about 4-months. Only one of those was detected by their antivirus protection. Security company Kaspersky reported that a global malware attack that stole individual’s data had eluded antivirus software for five years.
Globally, an estimated $8.4-billion is expected to be spent on antivirus software alone this year. So why doesn’t it offer better protection?
The reason is in the sheer volume of malware being produced. Kaspersky finds 200-thousand new pieces of malware every day, which means there are likely several thousand more being produced each day that avoid detection. That number is up significantly from only 700 piece of malware daily in 2006 and 7-thousand in 2011.
Keeping antivirus programs updated protects you from known threats, which means you’re safe from the majority of the malware that’s out there. However, there are varieties of malware that have been produced, but not yet discovered that pose a significant threat.
In addition to the unknown malware is new techniques by hackers that disables antivirus products all together. Security software is continually getting smarter to protect against these hacks, but it’s an uphill battle.
One way security is improving is to expand the capabilities of antivirus programs. Rather than scanning systems for known malware, they’re able to scan for suspicious behavior from any program, whether it is suspected of being malware or not.
Unfortunately, creating malware is a big, lucrative business. Security software will always be behind the curve in keeping up with new ways for hackers to attack your computer. To stay safe, it’s important to practice safe surfing. Be careful of what you download to your computer, don’t open emails you suspect to be spam and don’t click suspicious looking links.
Even though antivirus programs can’t offer impenetrable security, it is still vital to have updated security in place. To improve the security for your computer at home or at the office, call Geek Rescue at 918-369-4335. If you think you’ve already been infected with malware, we fix that too.




















