June 15th, 2021

“They’re watching my keystrokes?”
As cybersecurity threats become more vicious, they’re also becoming more cunning in the ways they capture data. While this is true, one of the most prominent is also one of the oldest data-stealing techniques — keylogger malware programs.
“What is a keylogger?”
Keyloggers are software systems designed to log keystroke data from a user’s computer and transmit them to a third party. Cybersecurity threats frequently hide keyloggers in malware programs to steal confidential information. Some of the most commonly stolen data points include passwords, banking information, and other sensitive items.
“Are there legitimate uses for keyloggers?”
Though commonly employed by cybersecurity threats, keyloggers may also have a legitimate application. For example, some business entities may use keyloggers to monitor employee computer usage as white hat spyware. Investigators may use keyloggers for user surveillance. Software developers and researchers may also use approved keylogger systems to study user experience.
While there are many legitimate uses for keyloggers, they have a propensity to be misused for cybercriminals.
“How does a keylogger work?”
Keyloggers are installed on the backend of a computer’s operating system or possibly an internet browser through a third party — either through an approved entity or without the user’s knowledge. Like many other malware programs, keyloggers are frequently downloaded due to a user clicking on a malicious link or downloading a file they believe to be harmless. Keyloggers can also be installed through an external hardware device — such as a mysterious flash drive — plugged into a computer’s USB port.
Once installed, depending on the particular software, a keylogger can capture and transmit everything from website form data and screen activity to even hijacking the cameras, microphones, or a device’s GPS information.
“How can I protect myself or my organization against keyloggers?”
Revisiting cybersecurity best practices is the best way to protect yourself or your workplace against keylogger infection.
Never connect to open wireless internet networks without proper protections. Also, make sure your wifi router is thoroughly password protected.
June 14th, 2021
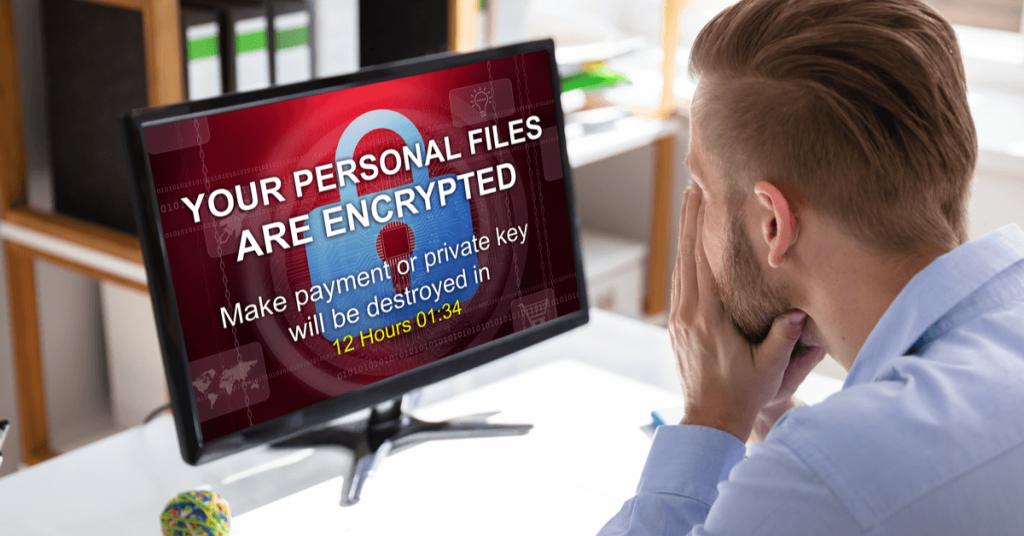
In spring 2021, Tulsa experienced one of the most significant cybersecurity events ever to strike the municipality — a ransomware attack. In addition to city communications, as of the writing of this piece in June 2021, some utility payment systems have not fully recovered.
“What is ransomware?”
Ransomware is software installed on an unsuspecting user’s devices — computers, phones, hard drives, and other affiliated equipment — with the power to remotely encrypt hard drives, applications, or even operating systems. The software essentially holds the data and systems hostage — requiring a passcode to unlock the systems and gain access to the information. Cybersecurity threats will usually demand a ransom in return for this passcode or the decryption of the data.
“How does one’s computer or system become infected with ransomware?”
The most likely infection method for an organization is via something called phishing. In a phishing scenario, an organization member with a device connected to a more extensive system will either accidentally or through manipulation download malware through an email attachment or some other access point. Either the individual clicks on what they believe to be a harmless email link or, in a spearphishing scenario, they’re deceived into downloading a file from a compromised source they would usually trust. There are other ways to be infected with ransomware.
“What do should I do if I suspect a ransomware attack has taken place?”
If you suspect that a ransomware attack has taken place or you’ve received notification requesting a ransom, there are some actions you can take to mitigate the damage. Firstly, you will want to segment your system by unplugging networked systems. Changing shared passwords may also be an excellent way to limit the rate of infection. Bring up any unfamiliar activities with your organization’s IT department.
“How can I reverse a ransomware attack?”
Sadly, there is no magic cure to ransomware attacks. Yes, malware scan systems are helpful, but they’re no match for behavior training — helping your employees manually vet links before they click them to limit exposure to cybersecurity threats. However, once infected, there is little you can do if a nefarious actor has control of your data. This is why ransomware prevention and preparation are key.
“How do I prevent ransomware attacks?”
- Behavioral training. Every member of your staff needs to be on high alert against phishing and spearphishing scenarios. Many make the mistake of only training those with access to sensitive data. However, those who share files with those individuals can be used as conduits for malware systems.
- Regular malware scans and security patch upgrades. Making system scans and security patch upgrades standard protocol is a great way to protect your organization’s system from deeply embedded malware programs.
- Automated and tested three-tier backup. According to cybersecurity professionals, your data is highly vulnerable if at least three separate sources don’t back it up. There are several different backup protocols a company or organization can put into use with the help of a managed IT provider. In addition, a robust data backup system helps reduce the chances of a cybersecurity threat taking monetary advantage of a company or organization through their sensitive data.
Remaining vigilant against ransomware is challenging but ultimately worth it.












