November 5th, 2013

We’ve mentioned before that you can’t ever be completely secure online. But, some actions you take make you more secure and significantly less likely to be hacked. Andy O’Donnell of About suggests a number of mistakes that are commonly made and how they can lead to hacking. Here’s a list of some of the most common, as well as how you can avoid making them.
- Not Using Unique Passwords
Why would you need more than one password for your online accounts? If you use a long, strong password that’s difficult to break, you should be safe, right? Actually, no. Not all accounts are compromised by a third party guessing or breaking your password. Sometimes, large lists of passwords are stolen from companies. If your password is the same on every site you have an account with, a criminal could now have access to all those sites, rather than just the one. If you’re worried about remembering all of those unique passwords, consider using a password manager.
- Using An Unsecured Wireless Network
Whether it’s at home or at the office, your wireless network needs to be secured to keep out intruders. First, make sure you’re using adequate encryption. Check your router’s settings and enable WPA2 based encryption, rather than the less secure WEP. Then, set a long, strong password using upper and lowercase letters, symbols and numbers. Try to avoid using things like pets’ or children’s names or birth dates because those are likely to be known, or able to be found out, by others.
If you receive an unsolicited email with an attachment, don’t download the attachment. It’s simple advice, but many users believe they can download the attachment to find out what it is. In actuality, they’re downloading malware, which immediately infects their system. The same goes with pop-ups. Even with a pop-up blocker active in your web browser, you may see pop-ups from time to time, especially if you’re on a questionable website. Clicking on these pop-ups will often start a malware download.
To be properly secured, you need an active antivirus program and a firewall in place. These have to be turned on to work. This seems obvious, but many users will disable them if their computer is running slow, or if they’re having trouble running another application. This is ill advised. Also, security software needs to be continuously updated. This is to enable to software to recognize the latest pieces of malware and viruses. If you fail to update your antivirus, it becomes less and less effective.
These common mistakes make you an attractive target for hackers. To improve your cyber security, or to fix the damage already done to a device by malware and viruses, call Geek Rescue at 918-369-4335.
November 4th, 2013
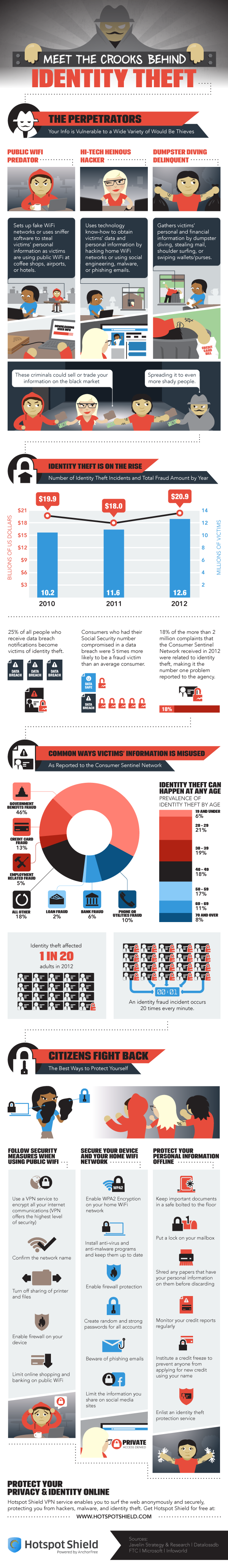
Protecting your computer from viruses and malware is only part of the concern of cyber security. Identity theft, which often begins with data being stolen over unsecure networks, through malware, or phishing scams, is also a costly threat.
Peter Nguyen, of the HotSpot Shield blog, writes that the number of identity thefts in the US is constantly growing. Last year, there were 12.6-million victims, which is enough for an identity theft to happen every 3-seconds. The financial loss of the victims totaled almost $21-billion.
The included infographic covers the how and why of identity theft. It also gives a few tips for how to stay safe. In addition to some offline measures, like shredding documents containing personal information, monitoring your credit reports, and locking your mailbox, here are the most important online safety tips.
- Beware public WiFi. When using an unsecured network at a coffee shop or other public place, limit your activity. Any transactions that require you to input financial information should wait. A firewall should be enabled on your device and you should turn off sharing of printers and files.
- Use proper security on your home wireless router. The router is your first line of defense, so make sure WPA2 encryption is enabled and a strong password is required to log on.
- Keep antivirus programs running in the background and keep them updated. Updating security software enables them to detect and protect against the latest threats.
- Keep social media profiles private. Every social network gives you options for what you share with whom. Make sure strangers don’t have access to information like your birthday, family information, phone number and employment history. This can all be used for identity fraud.
- Use long, strong passwords. Many security experts suggest passwords longer than 6-characters and using both upper and lowercase letters, numbers and symbols.
To improve the security of your devices at home, or at your business, call Geek Rescue at 918-369-4335. We not only fix devices, we also help keep them safe.
November 4th, 2013

What do you know about CrytpoLockers? As a post on the Integral IT blog reports, this relatively new form of computer virus is capable of gaining access to and encrypting files on your machine, which then makes it impossible for you to use them. In order to stay safe and minimize the damage, there are some precautionary steps that need to be taken.
CryptoLockers primarily gain access to your computer or network through email. They appear as a seemingly legitimate attachment. Once downloaded, they begin to wreak havoc.
Any file you have access to, a CryptoLocker will encrypt and damage. You’ll no longer be able to access these files. When you try to open them, you’ll be met with a warning that the file is corrupted and can’t be opened.
This warning is the first sign that you’ve downloaded a virus. Otherwise, the CryptoLocker operates in the background and is undetectable for most users.
To remove the virus, you’ll have to identify the file containing the CryptoLocker and delete it. Then, you’ll be able to restore the corrupted files from back-up, which you’ve hopefully kept current.
To avoid a catastrophic loss of data due to a CryptoLocker infection, keep a trusted, frequently updated antivirus program running on your machine. Allowing it to update constantly makes it more capable of detecting new threats like CryptoLockers before they do any real damage.
Be aware of threats like this when checking your email. Using attachments is a popular method of hackers for infecting a large number of users. Knowing this makes you more suspicious of emails containing attachments, especially when they’re unsolicited.
This is also a warning to keep your back-ups current and frequent. You’ll never be able to be immune to threats like this, so regularly backing-up vital files ensures that, even when disaster strikes, you’ll be able to recover quickly.
Geek Rescue offers security solutions for all of these issues and concerns. We remove existing viruses and malware, improve your security infrastructure to better protect against threats and offer data storage and back-up. Call us at 918-369-4335 to stay safe from threats like CryptoLockers.
October 7th, 2013

As previously mentioned, antivirus programs can’t be expected to fully protect your computer. Hackers produce hundreds of thousands of new malware every day and even the most up to date security software can’t possibly keep up.
That’s why it’s important to do your part and keep your machine out of harms way as much as possible. Shay Colson, of Information Space, has some tips on how to avoid malware and other potential threats online.
Just as in the forest it’s important to watch where you step, online it’s important to watch where you click. Most malware is downloaded to a computer when the user clicks on something they shouldn’t have. Particularly when you’re on a less reputable website, it’s important to avoid clicking on ads or links as much as possible. Also, make sure any security software you have installed is up to date. That way, if you do encounter malware, you’ll have the best chance of having it detected before it does any real damage.
The simple solution for making all of your accounts online more secure is to improve your password. Make sure it is 8-characters or longer and includes both upper and lowercase letters, numbers and symbols. Some advocate using your least secure passwords for throwaway accounts, medium passwords for social media, but if you want to avoid a potential hacking, use unique, strong passwords for each account. Using all of those different passwords can get confusing, so it’s also a good idea to use a password manager.
Almost everyone makes purchases online. It’s a good idea to use a credit card, rather than a debit card, however, since it’s easier to dispute fraudulent charges on a credit card. Most eCommerce sites give you the option to save payment information for your next purchase. This is a time saver, but it puts your account information at risk. It’s much better to enter your card number each time than have it available to anyone who gains access to your account.
Your mobile device also has access to sensitive data. Keep it safe by utilizing the lock screen. As seen with an iOS bug that allowed users to bypass the fingerprint scanner, or Android’s notoriously easily hacked lock, this doesn’t fully protect your device. However, it offers some protection and is easy to use. Also, be sure to enable services to remotely disable and wipe your phone in case it’s stolen. Both Apple and Android offer this service. It’s extremely useful in keeping your data out of a criminal’s hands.
These tips keep your information safe without installing additional security software. However, you should always have antivirus programs and other security in place. To improve the security on any of your devices, contact Geek Rescue at 918-369-4335. We also remove viruses and other malware from infected machines.
October 7th, 2013

It seems like everyday there’s a new story about a major company or website that’s been hacked or attacked by malware. Many times, as Steve Johnson of the San Jose Mercury News reports, these attacks stem from initial infections that slip past security software and remain undetected for days, weeks or even months.
The New York Times recently encountered 45 pieces of malware that had remained on their computers for about 4-months. Only one of those was detected by their antivirus protection. Security company Kaspersky reported that a global malware attack that stole individual’s data had eluded antivirus software for five years.
Globally, an estimated $8.4-billion is expected to be spent on antivirus software alone this year. So why doesn’t it offer better protection?
The reason is in the sheer volume of malware being produced. Kaspersky finds 200-thousand new pieces of malware every day, which means there are likely several thousand more being produced each day that avoid detection. That number is up significantly from only 700 piece of malware daily in 2006 and 7-thousand in 2011.
Keeping antivirus programs updated protects you from known threats, which means you’re safe from the majority of the malware that’s out there. However, there are varieties of malware that have been produced, but not yet discovered that pose a significant threat.
In addition to the unknown malware is new techniques by hackers that disables antivirus products all together. Security software is continually getting smarter to protect against these hacks, but it’s an uphill battle.
One way security is improving is to expand the capabilities of antivirus programs. Rather than scanning systems for known malware, they’re able to scan for suspicious behavior from any program, whether it is suspected of being malware or not.
Unfortunately, creating malware is a big, lucrative business. Security software will always be behind the curve in keeping up with new ways for hackers to attack your computer. To stay safe, it’s important to practice safe surfing. Be careful of what you download to your computer, don’t open emails you suspect to be spam and don’t click suspicious looking links.
Even though antivirus programs can’t offer impenetrable security, it is still vital to have updated security in place. To improve the security for your computer at home or at the office, call Geek Rescue at 918-369-4335. If you think you’ve already been infected with malware, we fix that too.
October 2nd, 2013

Your Facebook profile is an appealing target for cyber criminals. With access to your profile, they immediately have access to all of your friends also. A hacked Facebook account has led to the hacker asking for money from Facebook friends, posting malicious links on friends’ walls and other suspect behavior.
Andy O’Donnell, of About, notes that you’re usually not the first to find out you’ve been hacked. A friend may text you to ask about an odd status update or message. When you try to sign into your account, either you’ll notice that someone else has been posting messages as you, or you’ll be locked out completely. If you believe you’re account has been hacked, follow these steps.
- Go to facebook.com/hacked, which is the Facebook Account Compromise Reporting page.
- Click ‘My Account is Compromised.”
- You’ll be taken to the ‘Identify Your Account’ page where you’ll be asked to enter your email address, phone number, or your name and the name of a Facebook friend.
- Follow the on-screen instructions.
Once you’ve re-gained access to your account, you’ll want to un-do anything that the hacker did. First, change your password. Take this opportunity to make it stronger by using upper and lowercase letters, numbers and symbols. Check your apps page to delete any suspicious apps the hacker may have added. Be sure to tell all of your friends that your account was hacked so they don’t follow any links the hacker may have sent them.
After you’ve taken care of any issues on Facebook’s site, take some time to think about how your account was compromised. Malware on your computer can result in hacked accounts, so a full-scan of your hard drive may be in order.
If you believe your computer is infected with malware, call Geek Rescue at 918-369-4335. We remove malicious programs like malware, Trojans and viruses from any device and have security options to help protect you from future attacks.
September 30th, 2013

Creating an adequate, effective security infrastructure for your business is difficult. It becomes impossible, however, if you don’t take the time to consider where your weaknesses are.
Patrick Budmar, of ARN, reports that security experts estimate that 80-percent of IT security spending at an average company is focused on only 30-percent of the problem.
Firewalls, intrusion protection systems and endpoint security are noted as receiving the bulk of most security budgets. However, diverting funds to increase prevention and detection of threats is a more efficient practice.
Regardless of the amount of security software in place, there will be breaches and gaps in your security. That’s why experts recommend focusing more attention on monitoring data and constantly checking for abnormalities within your network. Many times, a security breach goes unnoticed for weeks or months at a time. This allows for an exponentially higher amount of damage than if the breach was detected immediately.
An audit of your company’s cyber security exposes the potential flaws. It also shows where more attention or funding is needed, and where funds can be diverted from. This way, you’re able to upgrade security by spending more intelligently, not necessarily by spending more.
Geek Rescue provides security audits and the tools needed to improve security. Call us at 918-369-4335 before an attack to avoid costly damage and data loss.
September 27th, 2013

Antivirus vendors are reporting that a new piece of malware is being used in infection attempts hundreds of times per day over the past few weeks. It goes by the name Napolar or Solarbot and is used to steal information.
Lucian Constantin, of PC World, writes that this new malware started infecting computers in mid-August, but was put up for sale to cyber criminals weeks before the first infection. For $200, hackers are able to buy the Napolar binary code and launch their own malware attack.
While infections have mostly been reported in South America so far, security experts fear this malware will spread quickly, due to its affordable price tag. It appears Napolar is being spread through compromised Facebook accounts.
Napolar is similar in functionality to a Trojan, which has been around for years. Experts speculate it could actually become more popular, however, because of its ease of use and because it is upgradeable with plug-ins.
The tell-tale signs of the malware are pop-up images of women appearing on screen after downloading an infected photo-file.
With more hackers purchasing Napolar and more Facebook users being infected, it’s only a matter of time before the malware reaches North America.
Be sure to keep your antivirus software updated. If you discover that your computer has been infected by malware, bring it to Geek Rescue. We disinfect any device and help you improve your security to protect against future attacks. Come by or call us at 918-369-4335.
September 25th, 2013

It’s easy to understand why so many hackers are targeting social media for cyber attacks. Where else would you find such a high collection of unsuspecting people? Many users have grown wise to email attacks and have learned to avoid suspicious emails. Social media, however, is still seen by most as a safe place. Throw in that many users access social media on mobile phones, which often lack necessary security, and you have an irresistible target for hackers.
John P. Mello, of CIO, reports that these attacks claim victims using the trust of users against them. Similar tactics as previously seen in creating fake versions of legitimate websites, or sending phishing emails that appear to be from legitimate sources, have been adapted for social media. The trend is to take over an account with a large number of followers and credibility and use it to spread malicious links.
These attacks are difficult to avoid because they appear to be coming from a trusted source. You wouldn’t expect a Twitter account that you’ve followed for years to suddenly be directing you to a phishing site, or infecting you with malware.
This isn’t only a concern for individuals either. Businesses need to be aware of these threats to security also. Another reason that social media is so attractive to hackers is that so many users access social media on their company’s network. This means that if any of your employees encounter a hacked profile, they are putting your company’s data at risk.
There are a number of options for how to deal with these threats. Blocking social media sites is one. Educating employees about the risk and making sure they understand how to avoid these attacks is another.
To improve your company’s security, contact Geek Rescue at 918-369-4335. We offer security software that is capable of blocking potentially dangerous sites and catching malware before it infects your system.
September 24th, 2013

Microsoft Windows users may be tempted to forego any additional security software because of the existence of Windows Defender, a free antivirus program included with Windows. While Defender does offer some security benefits, Mathew J. Schwartz, of Information Week, points out that it hardly is capable of protecting your computer on its own.
In a study conducted with 27 other antivirus programs that tested protection, repair and usability of each, Defender scored the lowest. In fact, out of a possible score of 18 on the test, Defender scored about 5 points lower than any other program.
In a test of about 60-thousand common pieces of malware, Defender was able to detect 97-percent of them. Not so good considering only three other programs failed to achieve 100-percent detection.
Defender does have its advantages, however. It earned top marks in usability and, of course, its price tag can’t be beat.
So, should you run Windows Defender on your computer? Absolutely, but you should have other security in place, as well.
Security experts suggest using multiple layers of security, even if you have the top ranked programs in place. Because malware is constantly changing and new forms are released each day, there’s no way any program can keep up. So, having multiple ways to detect malicious programs gives you a better chance to avoid infection.
For help improving the security on your machine, or to get rid of malware that’s already infected it, call Geek Rescue at 918-369-4335.




















