November 21st, 2013

Spam emails began as a nuisance, but one that ultimately wouldn’t harm your computer. Since those early days, spam has evolved to be much more malicious. Now, spam often is the first step to infecting your machine with malware, trojans, keyloggers and viruses. Spam can be used to steal your identity and hold your computer for ransom. Jeff Orloff of The Email Admin posted some threats to be on the look-out for and some tips for how to stay safe.
Cryptolocker is the latest threat making headlines. The trojan is a form of ransomware that first surfaced in August. Most commonly, it stems from an email attachment that infects the victims computer when it’s downloaded. The cryptolocker is then able to encrypt certain types of files on your system and holds them for ransom. To decrypt the data, a payment is required. Often, there is a deadline that goes along with this demand for money. While some users report they’ve paid the ransom and their files were encrypted, others have paid and seen no results. Unfortunately, even professionals struggle to decrypt files that have fallen victim to a cryptolocker.
In less than a week, more than 12-thousand users reported being infected by a cryptolocker in the US. This isn’t the only threat to your security that strikes through email. Cryptolocker is just the latest.
Email security is essential for both your business or your home network. There are a number of options for enhanced email security, but regardless of what you choose, make sure it includes some vital features. Your security software should scan incoming email for known threats and separate those that are potentially harmful. Email protection has to be more intelligent than ever to properly protect you. Spammers are constantly updating their tactics to get around spam filters.
Geek Rescue offers a number of options to keep you safe from the latest cyber threats. Call us at 918-369-4335 to find out how we can protect you.
November 21st, 2013

A laptop can be an expensive investment. On average, consumers expect to get at least three years out of their laptop before it either breaks down or becomes outdated. With that in mind, Adam Dachis of Lifehacker, published some factors and stats to consider before you make your next laptop purchase.
- How likely is it to break?
The last thing you want when you buy a laptop is for it to breakdown within a few months. A 2012 study addressed this concern to find what brands manufacture the most trustworthy laptops. Over the three year span the study covered, Asus computers broke the least, but that was still more than 15-percent of their laptops. Toshiba also performed well, while HP and Gateway computers were found at the bottom of the list. In fact, one out of every four HP laptops failed in less than three years.
A good experience with a laptop isn’t entirely centered on the performance of the machine itself. The time will likely come when you need some tech support, so you should consider what company provides the best service. Consumer Reports credits Apple with far and away the best tech support. Combined with reliability, that makes Apple products the best bet, followed by Asus. Acer/Gateway scored the worst in tech support, while scores for Sony were unavailable.
Sheer numbers don’t tell the whole story. While the statistics seem to suggest that Gateway and HP offer inferior products, they could still produce individual models that outperform industry leaders Apple and Asus. Be sure to check user reviews and pay attention to more than just the number of stars. If you have specific questions or concerns about a laptop, or need it to perform certain functions, look through reviews to find other users similar to you. Remember that most manufacturers make different laptops for different budgets. Just because one brand’s budget laptops are notoriously untrustworthy doesn’t mean their top of the line model isn’t worth the money.
By putting in some time to do the proper research before you buy, you can save yourself money and frustration later. Eventually, every computer encounters problems, however. When that happens, bring your device to Geek Rescue, or call us at 918-369-4335.
November 20th, 2013

When you enter a website’s URL and a page appears in your browser, you assume you’re in the right place. That might not always be the case, however. As Jaikumar Vijayan of Computer World reports, Man in the Middle attacks, or Border Gateway Protocol hijacking, reroutes internet traffic and is a growing problem.
About 1500 instances of these attacks have been observed in 2013. That’s a fairly low number considering the amount of traffic online each day, but it reveals that these attacks are possible and something users need to protect themselves from.
These attacks don’t permanently re-route traffic. That would immediately signal to the owner of sites they’re diverting traffic from that something is wrong. Instead, the hijacking of traffic is only temporary, sometimes only lasting for a matter of minutes.
Users who fall victim to these attacks find themselves on a different site than the one they intended to go to. Sometimes, that difference isn’t obvious, however. In many instances, criminals hijack traffic from banking websites. They also create a site that looks fairly similar, or at least passable, and then capture users log-in information. Unfortunately, many users assume they’re in the right place, so minor differences don’t alert them there’s a problem. Sometimes, just having a company’s logo and a place to log-in is enough to fool users.
Attacks like this are the reason many banks have put additional security measures into their log-in process. For example, many financial institutions include a picture and custom greeting for each user before they enter their password. If those don’t appear, users are warned not to log-in.
For individuals, the way to protect yourself from these attacks is to be aware of them and be cautious on any site where you are asked to log-in. Take a moment to look around the site and try to notice any differences from the site you’re used to visiting.
For website owners more precautions are needed to protect users.
For help adding security to your website, business network or personal computer, call Geek Rescue at 918-369-4335.
November 20th, 2013

Stolen smartphones are a big problem in the US. About one in three robberies involves a smartphone and lost or stolen phones total about $30-billion each year, according to the FTC. A possible solution, or at least a tool that could decrease the number of smartphone thefts, has been found, but as Daniel Johnson, of The Telegraph, reports, US carriers have refused to use it.
It’s called ‘Kill Switch’ and it allows phones to be disabled remotely in the event they’re stolen. The thinking is that criminals would be less likely to steal phones if they were immediately disabled and made worthless except for spare parts. Samsung liked the idea so much they began making smartphones with Kill Switch pre-installed. Those phones won’t be available in the US, however.
AT&T, Verizon, T-Mobile and US Cellular have rejected Kill Switch and forced Samsung to remove it from all phones set for distribution in the US. Their official stance is that Kill Switch could be used by hackers to disable phones that haven’t been stolen.
According to some industry insiders, however, the rejection of Kill Switch has more to do with the potential loss of insurance revenue. It’s believed that theft insurance would be less in demand if Kill Switch became standard on all devices. This thinking ignores the fact that insurance would still be useful for lost and broken phones, however.
The problem remains implementing a kill switch in a more secure manner. The possibility of hackers remotely disabling smartphones poses a serious problem, which won’t be easily solved given that Kill Switch is software and software is inherently hackable.
At Geek Rescue, we can’t stop your smartphone from being stolen. But, we can fix nearly any other problem you’re having with your device. For broken or unresponsive screens, slow performance, malware, or any other issue, call us at 918-369-4335 or bring your phone in to one of our locations.
November 19th, 2013

Do you have Silverlight installed on your computer? The Microsoft product, similar to Adobe Flash, is used for running internet applications, most notably the streaming video client on Netflix. Subscribers alone account for 40-million Silverlight users worldwide. As Zeljka Zorz of HelpNet Security reports, all of these users are at risk of becoming a victim of a malware attack that exploits a critical vulnerability in Silverlight.
The malware, which could allow remote code execution, finds it way onto your machine when you visit an infected website. This website could be specifically set-up by hackers to infect unsuspecting users, it could be a compromised site that’s infecting users without the owners knowledge, or a site that allows user submitted content.
When you land on one of these websites, an Angler exploit kit, which is a tool used by hackers, determines what version of Silverlight you have installed. It determines whether you are vulnerable to an attack and, if so, the malware is downloaded to your computer.
The reason the Angler is needed is because Microsoft has already released a patch that fixes the security flaw being exploited. However, a number of users fail to update and are still using out-dated versions of Silverlight. If you’re using Silverlight, be sure you update to close vulnerabilities that could otherwise lead to a malware infection. If you don’t use Silverlight, but have it installed, you can remove it completely to protect yourself from this attack.
This is another example of why it’s important to keep all applications up to date and install each patch when it’s released. Enabling automatic updates for trusted applications makes this job easier.
If you have experienced a malware attack and your computer’s performance is suffering, bring your machine to Geek Rescue or call us at 918-369-4335.
November 19th, 2013

Recently, we talked about how to get the most out of OS X Mavericks, the newest operating system for Mac. There are plenty of tips for PC users too. Whitson Gordon, of Lifehacker, published a list of tips for Windows Explorer to help you organize and navigate your files and folders more efficiently.
- Change the way files are sorted
If you’ve spent much time using Windows Explorer you’ve probably noticed that there are a few different options for how to sort files and folders. If you know where to look, you can customize each folder to display exactly how you want it. While in a folder, click the ‘View’ tab and you’ll be rewarded with plenty of options. To set one as the default, rather than just a one-time change, go to ‘Options’ and ‘Change folder and search options’ from the ‘View’ tab. Then, from the open menu, select the ‘View’ tab and choose ‘Apply to folders’. This will make it a universal change for each folder in Explorer.
To select multiple files at once, you can always hold ‘Control’ while clicking them. But, all of your selections will be lost once you click without first pressing ‘Control’. That can get frustrating. Instead, use a little known Explorer feature. Go to the ‘View’ tab and select the ‘Item Checkboxes’ box. Now, hovering over a file will reveal a small box to the left of the file name that can be checked to select.
There are a few shortcuts you can take in Explorer if you know the right combination of keys to press. This saves time and eliminates the need to go hunting through menu options. Here are some of the most useful.
‘Windows’ key and ‘E’ launches Explorer.
‘Alt’ and ‘D’ or ‘Control’ and ‘L’ select the address bar.
‘Alt’ and ‘P’ shows or hides the preview pane.
‘Alt’ and ‘Enter’ shows the properties of the currently selected file.
- Change the starting point
Explorer comes with a default starting point you’ll see every time you open it. Depending on the version of Windows you’re using, this could be the Libraries folder, This PC folder or My Computer. If you’re constantly having to go through multiple folders to get what you want, you should consider changing Explorer’s starting point. If you’re not using Windows 8.1, you can just go to Explorer’s properties menu and change the ‘Target’ bar to the address of the folder you want to start on. In Windows 8.1, it involves creating a new, custom Explorer short-cut and a short snippet of code.
Windows Explorer is a powerful tool that allows you to quickly access any file on your PC. With these tips, it becomes easier and more efficient to use.
At Geek Rescue, we know computers. If you’re having problems with yours bring it to us, or call us at 918-369-4335. We get rid of malware or viruses, repair hardware and more.
November 18th, 2013

Computers aren’t cheap and most of us see a decline in performance of our current PC before we’re ready to invest in a new one. A post at IT Manager Daily contains some suggestions for how to improve the performance of older computers to prolong their life. Whether you want to get more out of your personal laptop, or don’t have the budget for new computers at your business, these are valuable tips.
If your PC is a couple years old, you’ve probably downloaded files and applications you don’t need. You’ve probably also encountered malware, adware or spyware that is still on your hard drive. There are tools available to do a complete scan of your system and help you remove unwanted and unnecessary files. Once you also remove the files and programs you no longer want or need, be sure to run Defrag, or defragmentation. This reorganizes data stored on your hard drive to make it more efficient. Over time, fragmentation occurs when files are saved and deleted.
At this point, you should have deleted everything that isn’t vital on your machine. Take what’s left and back it up on an external hard drive or another storage device. This is to make sure nothing is lost through the rest of the process.
New hardware, like a memory upgrade, is much cheaper than an entire new computer, but will significantly improve performance. Do some research or ask a professional about which upgrades will boost your machine’s performance the most.
With everything backed up, you can start over from scratch. Re-install your operating system, or take this chance to upgrade to one with better performance. Be sure to check for updates that you may have failed to install before. These updates often solve stability issues that could be slowing down your machine.
Once you’re back up and running, be smart about what you save on your hard drive to keep it running smoothly for longer. Use cloud storage so you don’t have to save directly to your hard drive. Keep security software updated and running to keep viruses and malware from infecting your system. Regularly go through your files and delete those you no longer need.
If you need help upgrading hardware, installing a new operating system, backing up data or removing viruses and malware, bring your computer in to Geek Rescue, or call us at 918-369-4335.
November 18th, 2013

At this point, your phone is probably your most prized possession. You probably even feel strange if it isn’t with you. You can use your smartphone for almost anything, which means that the battery doesn’t last as long as you’d like. Jennifer Jolly, of USA Today, has some tips for how to get the most battery life out of your smartphone. These tips don’t even require you to sacrifice performance.
- Get Rid Of The Unwanted Features
Many of us don’t use our phone with bluetooth. You might not be in range of WiFi or in need of GPS services. There are features on your phone that you either never use, or only use in certain situations. If you need to get more life out of your smartphone’s battery, turn these services off until you want to use them.
Your smartphone’s display drains more battery than anything else. Turning down your brightness settings can have a significant impact on your battery. In most settings, even the lowest brightness setting is easy to see and you’ll get a much longer battery life out of it.
Many users leave their smartphones on vibrate all of the time. That saves you from being the annoying person whose ringtone goes off in a meeting, but it drains your battery. Yes, it takes more battery to vibrate than it does to ring. If you’re desperate for more battery life, you’ll have to live with your ringtone.
Free apps are riddled with advertisements. It takes battery power to download and display those advertisements. So, pay the money for the full version that’s ad free and you’ll get a slight uptick in battery life. This is only helpful for apps you use often. Otherwise, you probably won’t see enough extra battery life to warrant the payment.
Keeping apps updated is also helpful for lowering battery life because many updates make apps more efficient. But, allowing your phone to auto-update is wasteful to the battery. This is because your phone is constantly checking to see if an update is available. Instead, just try to remember to check for updates on your own when it’s convenient.
With these tips, you can keep your phone from dying in the middle of the day.
If you have problems more severe than a dying battery, call Geek Rescue at 918-369-4335. We fix all brands of smartphones.
November 15th, 2013

It seems like every week a large-scale password theft makes headlines. The latest was Adobe, who experienced the loss of about 150-million user log-ins. Michael Santarcangelo, of CSO, writes that anytime a large batch of log-in information is stolen it jeopardizes the security of other businesses. There are three steps that should be taken in this event to keep your business secure.
- Check The Email Addresses
When an attack of this nature occurs, the compromised log-in information is made public. If you know where to look, you can look through the list of stolen log-ins for email addresses in your domain. This is important because if an employee had information stolen for one account, it significantly increases the likelihood that their other accounts could be compromised. This could lead an attack to your network. If you see one of your addresses in the list of compromised accounts, be sure to notify the owner of the address, then change their log-in information for your network.
Every password that was stolen is now in a hacker’s database. That means that any individual who uses the same or similar password as a user who had their account compromised is now in danger. Hackers will use these learned passwords to launch more informed, intelligent attacks on accounts. Check your company’s log-ins for similar passwords and get them changed immediately.
Be sure to explain to the affected employees why their account log-ins need to be changed and how a hacker could attack them. Giving them access to better information and training could prevent an attack in the future.
Few business owners understand that the loss of a large group of log-ins and passwords, such as the Adobe situation, could affect them also. Taking these precautions is labor-intensive, but necessary for security.
For help protecting your company from a devastating cyber attack, contact Geek Rescue at 918-369-4335.
November 15th, 2013
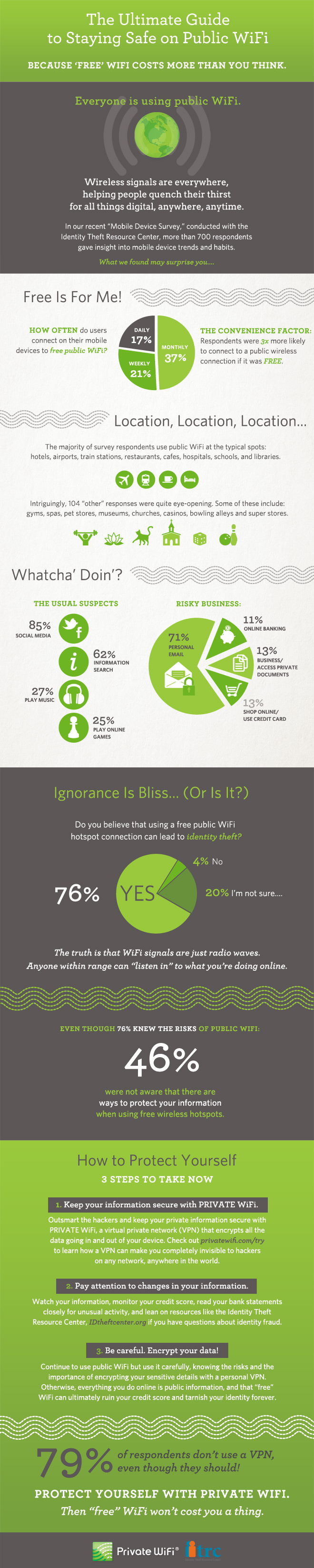
Free, public WiFi is offered nearly everywhere. Whether you’re at a library, coffee shop, restaurant, hotel, airport or hospital, you’ll be able to stay connected. That free WiFi comes with some inherent risks, however. PrivateWiFi and the Identity Theft Resource Center teamed up to produce this infographic, which details the general feelings about free WiFi and how you can stay secure while using it.
More than three-quarters of users understand that public WiFi isn’t secure. That’s the first step in a safer experience because those users will know not to log-in to their personal email or banking site while using an unsecured network. These safe surfing tactics aren’t the only way to improve security, however.
If a public network is unsafe, then why not use a private network? Even when connected to public WiFi, you can use a VPN to immediately improve security. There are a number of VPNs available. While many require a paid subscription, some are free up to a certain point. The VPN encrypts data being sent by your device and the data being returned to it.
A good idea is to keep close tabs on your online accounts, your financial information and your credit score regardless of the kind of network you’ve been using. But, it’s especially important to monitor your information if you know you’ve been on a public network. You probably won’t know immediately if someone hacks into your bank account or steals your identity. Regularly checking this information will save you from devastating damage because you’ll be able to recognize the first signs of trouble.
Understanding what’s at stake and when your information is most vulnerable is an effective way to stay more secure. When using free WiFi, try to avoid any site that require you to log-in. If you absolutely must log-in over an unsecured network, look into putting a VPN in place before doing so.
With more and more free wireless networks available, it’s more important to learn how to safely use them.
For more help improving the security of any of your devices at home or at the office, call Geek Rescue at 918-369-4335.




















