November 14th, 2013

Virtualization is becoming a staple of businesses of every size. According to a Cisco survey, 77-percent of small to medium businesses have already virtualized part of their infrastructure. In the next two years, the virtualization budgets will increase for about 70-percent of all businesses. As Sam Narisi, of IT Manager Daily writes, virtualization allows companies to save money while increasing flexibility and scalability, but there are some security concerns. Here are the top three security issues associated with virtualized services and how to overcome them.
Many organizations host multiple virtual machines on a single physical machine. This is the nature of virtualization and why it is so popular. This opens the door for devastating attacks, however, if the virtual machines aren’t properly separated. It’s important to grant employees access to only the VMs they need. This way, if their access is compromised, your entire virtualized infrastructure isn’t.
Any software will contain bugs and vulnerabilities that can be exploited by intelligent hackers. Virtualization software is no different, but allowing a hacker to use these vulnerabilities could prove much more costly than other software exploits. Patches and updates are constantly being made available to fix these flaws. It’s important to stay current and update your software each time a new patch is released so you can close holes in security before an attack takes advantage of them.
More than ever before, it’s important to have a firm grasp on the IT assets in existence and who has access to each in your company. This was a simpler job when each machine was physical. With virtualization, VMs can be created and moved quickly, which sometimes leaves IT out of the loop. If a problem comes up, it’s much easier to solve it when you know where each machine is and who is able to access it.
Virtualization offers a number of benefits for businesses, but it also comes with increased responsibility and security concerns. Geek Rescue helps take the uncertainty and labor out of virtualization. Call us at 918-369-4335 to find out what services will give your business a competitive advantage.
November 11th, 2013

A zero-day exploit that affects Internet Explorer, Windows XP and Windows 7 users won’t be getting a patch from Microsoft any time soon. Microsoft’s Patch Tuesday for November is only a day away and, as Paul Ducklin of Naked Security reports, news is already spreading that a patch for this exploit won’t be included.
The “remote code execution vulnerability” is dubbed a zero-day because hackers were the first to discover it. Rather than security experts, or Microsoft themselves, discovering the vulnerability and patching it, cyber criminals have been able to launch attacks in the wild before any precautions could be taken.
The attacks seen so far that exploit the vulnerability use .TIFF image files that contain malware. When a user opens the seemingly innocent image file, malware infects the machine, but no warning or notice is given. This silent infection allows hackers to remain undetected while they claim access to files and control a computer remotely.
So far, most of the attacks stem from email attachments. The .TIFF is hidden in a Word document and automatically loaded when the document is opened. There are a number of other ways the exploit could be attacked, however. Inserting the infected image file directly into the body of an email could infect your system through only a preview of the message. Hackers could also set-up websites specifically to infect visitors, or insert malware into existing sites using .TIFF images.
While there’s no patch coming from Microsoft this week, there are ways to protect yourself. A Fix it tool released by Microsoft will tell your computer to stop processing .TIFF files. This is a broad stroke, but one that will ensure the vulnerability will be closed until a more permanent patch is made available.
In the meantime, some simple advice will also help improve your security. You should always be wary of unsolicited emails and their attachments. Often, all it takes is opening the email to try to verify its authenticity is all it takes to become a victim. Also, make sure you have an antivirus program in place and it’s updated. Because of the way this exploit gives a hacker access to all of the files you’re current user account is able to access, it’s useful to use a non-administrator account. That way, if you are attacked, only part of your system is at risk, and solving the problem from an administrator account is much easier.
If any of your devices are infected with malware, bring them to Geek Rescue or call us at 918-369-4335. We’ll find the problem, fix it and help you protect yourself from future attacks.
November 11th, 2013

Software companies like Microsoft, Apple and Adobe release patches regularly to fix bugs and close security vulnerabilities. This is a common practice, but as Tyler Reguly of TripWire’s State of Security blog reports, Microsoft often makes a mess of it.
There are a number of factors that contribute to the confusing nature of Microsoft’s patch practices. Patch Tuesday occurs once a month and involves the patching of multiple Microsoft products and fix multiple vulnerabilities at a time. The downside to this bulk patch release is that new vulnerabilities that crop up are left open for weeks while users wait for the next Patch Tuesday to come around. There have been instances in the past when Microsoft has pushed out a patch outside of this schedule and other companies follow a similar patching process, but users are still left in the lurch from time to time.
In addition, patches are far from uniform. Microsoft could release multiple patches to fix a single vulnerability in a single product, or they could release one patch per product for each instance of a vulnerability. Some patches replace older patches, but sometimes multiple patches are needed to replace a single patch.
In an attempt to simplify this process, Microsoft introduced a single service that would automatically update Windows users with any applicable patches for all Microsoft products in use on their device. This actually caused more confusion, however. A user who has enabled automatic updates might think they’re fully patched at all times, but that’s rarely the case. That’s usually because an older version of an application is being used that Microsoft no longer supports or that won’t work with automatic updates.
Unfortunately, users aren’t warned that applications aren’t being updated. Instead, it appears they’re patched and safe from vulnerabilities. In many ways, this makes them more susceptible to breaches than if they knowingly avoided all patches to begin with.
Keeping your devices and networks safe requires an investment. Geek Rescue offers help for improving security for your home or business. Call us at 918-369-4335.
November 8th, 2013

About a month ago, software company Adobe announced that hackers had gained access to passwords and log-in information for millions of accounts. Initially, the number of accounts affected was estimated to be around 38-million. As Jim Finkle reports at NBC News, that number is actually significantly higher.
Password security firm, LastPass, discovered the stolen customer data on a website for cyber criminals. In actuality, 152-million user accounts were compromised.
Adobe, which makes popular software like PhotoShop and Acrobat, downplayed the significance of the data breach. They claim many of the accounts who saw their log-in information stolen were inactive. Either the email or password was out of date, or the account was registered under false information in order to take advantage of one-time free use offers. The out of date log-ins total an estimated 43 million accounts. It’s unknown how many accounts were set up with fictitious information.
Still, Adobe has notified 38-million users that their accounts may have been compromised.
Regardless of whether the log-ins were up to date or not, security experts warn that the data stolen is still valuable to criminals. The data stolen can be used in phishing scams with relevant details included to make them more believable. There’s also the concern of Adobe passwords being used for other accounts. As one expert pointed out, a user may have registered with Adobe years ago and since let the account become dormant. However, they may use the same password for other online accounts, which a hacker could now have access to.
Some have suggested that Adobe didn’t do enough to safeguard customer’s data from an attack. While this is an example of what can happen when the proper security isn’t put in place at the business level, there’s also a wake-up call here for users. Regardless of how strong your password is, it’s still vulnerable. Hackers have a variety of ways of breaking into your accounts, and they don’t all involved brute force efforts to guess passwords. Also, failing to use unique passwords for each account leaves you much more vulnerable to hacking.
If you have a business that needs to improve your security to keep your data and your customer’s data safe from attack, or if you’d like to improve the security on your personal devices, call Geek Rescue at 918-369-4335.
November 8th, 2013

One of the most common complaints about Google’s popular web browser, Chrome, is its inordinate number of security vulnerabilities. As Gregg Keizer reports for Computer World, Google is doing its part to close up one of the most noticeable flaws in its security by no longer allowing the installation of extensions that aren’t in the Chrome Web Store.
Currently, users can browse the Chrome Web Store for extensions, which other browsers call add-ons, much the same way you would browse for apps on your smartphone. These extensions grant the browser additional capabilities. Extensions have also been found outside of the Web Store. Some third party vendors offer Chrome extensions directly on their site’s, or included in downloads of their applications. Some companies have even engineered their own extensions specifically for their employees. Under Google’s new rules, these third party extensions would no longer be accepted by Chrome browsers.
The reason for this move is that it keeps users from accidentally downloading malicious extensions. By limiting users to only installing extensions from the official Web Store, Google is able to police all extensions available and remove those that contain malware or act maliciously.
Android hasn’t yet made the same move to limit users to only apps found in the Play store, but they do recommend that users stick to those apps. Otherwise, users risk infecting their devices with apps that haven’t been officially approved by Google.
This move for Chrome has been in the works for some time. When Chrome 21 launched in 2012, it no longer accepted extensions installed directly from a third party website. Earlier this year, Chrome again tightened extension security by adding a feature that blocked silent installations of extensions and disabled those already installed. This closed a vulnerability that allowed hackers to install extensions without a users knowledge. Usually, this was done in response to another user action to download from an untrusted source.
In order to completely close any remaining loopholes, Chrome has now gone to a strict policy of only allowing extensions directly from the Web Store. That doesn’t mean, however, that independent developers, and those developing extensions for company use, can’t continue to use their own extensions. The Web Store offers an option to hide extensions from the public and only make them available to those they’re intended for. Extensions will also still be available to download directly from third party sites, as long as the same extension has also been added and approved in the Web Store.
These changes aim to make Chrome a more secure browser. To upgrade your security at home or at the office, contact Geek Rescue at 918-369-4335.
November 7th, 2013

What do you know about threat feeds? These are a real time warning system that allow security teams to take necessary precautions to prevent the latest threats. They can be an incredibly useful resource for protecting your business. As Eric Ogren, of Computer World, points out, however, you may not have the necessary resources to adequately use threat feed. Instead, they might be best left to a third party vendor who handles your security.
- Find Threats Specific To Your Business
A threat feed isn’t tailored to you specifically. Instead, it’s a broad view of the latest threats in the wild. So, part of the investment involves combing through these feeds with a knowledge of your IT infrastructure and being able to recognize the threats that pose the biggest danger to you. This takes time and a high level of expertise. If you have both of these, a threat feed can serve you well. If you don’t, you’ll probably be better served letting a third party handle it.
- Developing Your Own Protection
Once you’ve discovered threats that are dangerous to you, you’ll want to protect against them. That means developing your own anti-malware signatures and patching your own security. These are the same types of actions an antivirus program would take, but you’ll be able to roll them out faster. That is, if you have the resources and knowledge available.
- Do You Have The Resources?
As mentioned, threat feeds present an opportunity to stay ahead of cyber attacks by recognizing the latest threats to your business. You have to have the capabilities to not only identify these threats, however, but also to take action to prevent them. If your team is capable, threat feeds should become a staple of your security.
If you’d like to leave your company’s security in the hands of the professionals, call Geek Rescue at 918-369-4335. We’re equipped to protect you against the latest threats and keep your data secure.
November 7th, 2013

There are many reasons to protect against cyber attacks. You need to protect your data, and your customer’s information, from third party criminals. You also want to avoid downtime, which prevents your customers from accessing your services or your employees from working. There are many issues involved in the fallout of a cyber attack, but the most telling is the monetary cost to your business. Jesmond Darminin, of IT News, reports that the cost associated with cyber attacks has grown for the fourth consecutive year. In addition to the costs, the frequency of attacks and the time it takes to resolve them are also on the rise.
The Ponemon Institute conducted their initial Cost of Cyber Crime Study four years ago. Since then, the cost has increased by 78-percent to an annual cost of more than $11.5 million on average, per company. In the past year alone, the average cost increased 26-percent, or $2.6-million more per attack. The companies involved in the study reported a range of costs between $1.3-million to $58-million. The average cost to overcome a single attack has reached $1-million.
During the same four-year time span, the amount of time it takes to overcome a cyber attack has also increased significantly. It takes nearly 130-percent longer to resolve a cyber attack now than it did in 2009. Companies reported it took an average of 32 days to resolve an attack. During this time, companies suffered a loss of about $33-thousand per day.
These increases can be attributed to more intelligent, sophisticated cyber attacks. More attention to security is needed than ever before and when an attacker finds a vulnerability, they’re able to do more damage and remain undetected for longer.
Companies suffered an average of 122 successful attacks per week, which is skewed by larger enterprises, but still illustrates the severity of the situation. Even though smaller businesses will likely experience fewer cyber attack attempts, once they become successful, they’ll likely begin to experience more.
That’s why a robust and effective security infrastructure is vital for your business. For help keeping your company safe, or for help recovering from a successful attack, call Geek Rescue at 918-369-4335.
November 6th, 2013

If you have an Android smartphone, you’ve probably noticed that there are a number of apps that came pre-loaded on it that you don’t need and don’t use. These apps come from the phone’s manufacturer, but as Liam Tung of ZDNet writes, they may be creating vulnerabilities in your smartphone’s security.
Researchers at North Carolina State University examined pre-installed apps on smartphones made by Google, Samsung, HTC, LG and Sony. Of the 10 devices studied, 86-percent of pre-loaded apps requested more permissions than they actually used. This gives the apps access to data they don’t need, but that data becomes accessible when the app is compromised.
In terms of sheer number of vulnerable, pre-installed apps, the HTC Wildfire S and the Samsung Galaxy S2 had the most of the pre-2012 devices. For post 2012, the Samsung Galaxy S3 contained a stunning 40 vulnerabilities. In contrast, Google’s Nexus 4 only had three vulnerabilities.
Google itself has a good track record for releasing security patches to fix vulnerabilities found on their hardware. However, for individual manufacturers like Samsung, Sony and HTC, these patches take time to roll out to customers. For the devices studied, an average of 6-months is how long it took for an officially released security patch to finally make it to all affected customers. That amount of time leaves a large window for hackers to exploit those vulnerabilities.
Some of these native apps are able to be removed by users, but many others cannot be. This means users stay at risk until an appropriate security patch is released to fix the problem. So, next time you’re in the market for a new Android smartphone, be sure to consider how many pre-installed apps it comes with.
At Geek Rescue, we remove malware, fix broken hardware and improve security on all kinds of devices, including smartphones. Whatever your issue, call us at 918-369-4335 or stop by one of our locations.
November 5th, 2013

We’ve mentioned before that you can’t ever be completely secure online. But, some actions you take make you more secure and significantly less likely to be hacked. Andy O’Donnell of About suggests a number of mistakes that are commonly made and how they can lead to hacking. Here’s a list of some of the most common, as well as how you can avoid making them.
- Not Using Unique Passwords
Why would you need more than one password for your online accounts? If you use a long, strong password that’s difficult to break, you should be safe, right? Actually, no. Not all accounts are compromised by a third party guessing or breaking your password. Sometimes, large lists of passwords are stolen from companies. If your password is the same on every site you have an account with, a criminal could now have access to all those sites, rather than just the one. If you’re worried about remembering all of those unique passwords, consider using a password manager.
- Using An Unsecured Wireless Network
Whether it’s at home or at the office, your wireless network needs to be secured to keep out intruders. First, make sure you’re using adequate encryption. Check your router’s settings and enable WPA2 based encryption, rather than the less secure WEP. Then, set a long, strong password using upper and lowercase letters, symbols and numbers. Try to avoid using things like pets’ or children’s names or birth dates because those are likely to be known, or able to be found out, by others.
If you receive an unsolicited email with an attachment, don’t download the attachment. It’s simple advice, but many users believe they can download the attachment to find out what it is. In actuality, they’re downloading malware, which immediately infects their system. The same goes with pop-ups. Even with a pop-up blocker active in your web browser, you may see pop-ups from time to time, especially if you’re on a questionable website. Clicking on these pop-ups will often start a malware download.
To be properly secured, you need an active antivirus program and a firewall in place. These have to be turned on to work. This seems obvious, but many users will disable them if their computer is running slow, or if they’re having trouble running another application. This is ill advised. Also, security software needs to be continuously updated. This is to enable to software to recognize the latest pieces of malware and viruses. If you fail to update your antivirus, it becomes less and less effective.
These common mistakes make you an attractive target for hackers. To improve your cyber security, or to fix the damage already done to a device by malware and viruses, call Geek Rescue at 918-369-4335.
November 4th, 2013
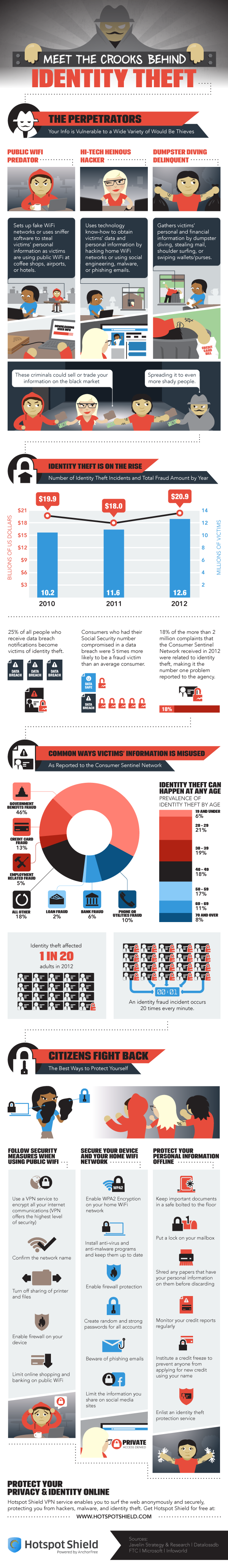
Protecting your computer from viruses and malware is only part of the concern of cyber security. Identity theft, which often begins with data being stolen over unsecure networks, through malware, or phishing scams, is also a costly threat.
Peter Nguyen, of the HotSpot Shield blog, writes that the number of identity thefts in the US is constantly growing. Last year, there were 12.6-million victims, which is enough for an identity theft to happen every 3-seconds. The financial loss of the victims totaled almost $21-billion.
The included infographic covers the how and why of identity theft. It also gives a few tips for how to stay safe. In addition to some offline measures, like shredding documents containing personal information, monitoring your credit reports, and locking your mailbox, here are the most important online safety tips.
- Beware public WiFi. When using an unsecured network at a coffee shop or other public place, limit your activity. Any transactions that require you to input financial information should wait. A firewall should be enabled on your device and you should turn off sharing of printers and files.
- Use proper security on your home wireless router. The router is your first line of defense, so make sure WPA2 encryption is enabled and a strong password is required to log on.
- Keep antivirus programs running in the background and keep them updated. Updating security software enables them to detect and protect against the latest threats.
- Keep social media profiles private. Every social network gives you options for what you share with whom. Make sure strangers don’t have access to information like your birthday, family information, phone number and employment history. This can all be used for identity fraud.
- Use long, strong passwords. Many security experts suggest passwords longer than 6-characters and using both upper and lowercase letters, numbers and symbols.
To improve the security of your devices at home, or at your business, call Geek Rescue at 918-369-4335. We not only fix devices, we also help keep them safe.




















