December 2nd, 2013

When you visit your bank’s website, most retailers or a credit card’s website, you might notice that the address starts with “HTTPS”. The added ‘S’ stands for secure. That’s ‘Hypertext Transfer Protocol Secure’ all together. It denotes that the site you’re using is safe from hackers stealing your log-in information. While that may have been true at one time, Rohit Sethi writes for USA Today that HTTPS alone no longer provides complete security for users.
HTTPS remains a useful tool to keep users secure, but it can’t do the job alone. Hackers have already exposed some areas of weakness. In another two to five years, successful attacks on HTTPS could become so common that an entirely new structure will be needed.
When using a site with HTTPS, your data is encrypted so that no third party will be able to steal it. However, attacks have already taken place that allow hackers to bypass this security. This means that log-in information for important online accounts, like for banking sites, is easily stolen by criminals in less than a minute. For both websites and users, this poses a particular problem because both parties believe in the security HTTPS is supposed to provide.
Users must understand that an HTTPS included in a URL and a small lock icon no longer provides enough security. Fortunately, there are other ways to keep your data safe. A Virtual Private Network, VPN, is one valuable tool. It provides an extra layer of encryption for all of your browsing activity. Many VPNs contain the same type of security flaws that have been exploited in HTTPS, so do some research and find a VPN using IPsec.
Smart, safe surfing habits also go a long way in protecting your data. Unsecured wireless networks provide little security, so if you’re using one, don’t log-in to any of your online accounts. Also, consider having a credit card dedicated to online purchases. This way, if that card is compromised, a criminal won’t have access to your entire bank account and you should notice quickly.
If you’d like to improve security for any device at home or at the office, or if you need to upgrade security for your website, call Geek Rescue for help at 918-369-4335.
November 29th, 2013

Buying a new computer is a great feeling. You get to start fresh with plenty of available storage space and you know there’s no malware or viruses slowing down performance. In order to keep your computer working properly and staying new for as long as possible, there are a few things you need to do as soon as you boot up for the first time. Andy O’Donnell of About lists the initial steps you should take with any new computer to ensure it’s secure and protected.
Your computer may be brand new, but that doesn’t mean the operating system and browser your using are up to date. Chances are there are updates to download and security patches to install. Without installing these, you leave yourself vulnerable to bugs and known holes in security that hackers can easily take advantage of. Your new computer won’t stay new for long if you fail to keep it up to date.
The first thing you should install on any new device is software to help keep it secure. There are a number of antivirus programs available for free, or a small fee. An anti-malware program is also helpful and a firewall is essential. Ideally, you’ll be able to research the best programs available before you boot up your new computer. That way, you’ll be able to download them quickly and you won’t be unprotected for long. As with your OS and other applications, it’s vital that you keep all security software updated and patched to keep it as effective as possible.
Once you’ve put protective measures in place, you’ll want to plan for disaster. Even with security software and updates installed, there are still plenty of ways to lose important data. Hackers, natural disasters and theft are all still possible. So, put a plan in place to regularly back-up your most important data to ensure that, even in a worst case scenario, you’ll be able to restore files as quickly as possible.
For help with any of these important steps with your new device, bring it to Geek Rescue or call us at 918-369-4335. We also fix computers to save you from having to purchase a new one.
November 29th, 2013

There are a number of precautions you need to take in order to stay safe online. From firewalls to updated antivirus software, there are plenty of tools that can prevent a disastrous cyber attack or data breach. These tools still don’t guarantee your safety, however. Even with precautions in place, it’s important to understand where the majority of threats come from and avoid them altogether with safe surfing techniques. Ron Johnson, of Business2Community, listed some of the most common causes of security breaches and how to avoid them.
Open WiFi networks are found nearly everywhere you go, but they’re far from secure. Any data you send over public WiFi is easily intercepted and stolen by a third party. This doesn’t mean you shouldn’t ever connect to public WiFi. It means you need to be extra careful about what sites you access while using this type of unsecured network. Viewing and reading websites likely won’t cause a problem, but don’t log-in to any online accounts or your password could be compromised.
Most users understand the dangers in giving other people their password, but sometimes even the most savvy users give out their log-in information without even thinking about it. For example, if you’re having difficulty with an account, a customer service representative might ask you for your password. This doesn’t necessarily mean they are going to misuse it, but it’s always a good idea to change passwords once you’ve told them to anyone, including a help desk. They might not always be as careful with your information as you would be. It’s also never a good idea to share accounts with others, even friends or family. If you want to allow another individual to access your account, change the password, give them the new log-in information, then change it again once they’re finished.
Downloading anything should be a decision that every user is cautious of. Even seemingly trusted websites can be compromised and a file you download could end up infecting your system with malware. If you’re prompted to download an application, like a media player, go to that player’s official website to download. Be sure to scan every file downloaded with your antivirus program before opening. As for email attachments, don’t download them unless you were expecting a file to be sent to you and you know exactly what it is.
Speaking of email, phishing scams are a popular method for stealing your information and hacking into your online accounts. These scams have grown more sophisticated. Often, an email will appear to be from a legitimate website where you hold an account. It will claim there’s been a problem and you need to log-in immediately, or download software, or even put in credit card information. If you have any questions about the legitimacy of these emails, contact the website or business directly, by phone if possible. There’s never a time when a business will email and need your credit card information.
By learning some of these common hacker tactics, you’ll be able to be smarter about your online habits and avoid potential threats.
If you’d like to improve security at your home or business to further safeguard from malware, phishing scams, hacking and more, contact Geek Rescue at 918-369-4335.
November 27th, 2013

A new piece of malware, a trojan called ‘Neverquest’, has security experts scrambling and forecasting a number of future attacks. As Lucian Constantin of Computer World reports, Neverquest has the ability to spread quickly and steal your financial information.
It’s believed that the Neverquest trojan originated in July, but the first attacks didn’t occur until months later. Now, experts have spotted thousands of uses of Neverquest and they expect to see that number spiral out of control soon.
In many ways, Neverquest is similar to other malware that targets financial websites. It’s able to insert its own forms into websites opened in Internet Explorer and Mozilla Firefox. It steals log-in information entered into these malicious forms and can also control your computer remotely.
Those are scary features, but that’s not all Neverquest can do. The trojan comes with 28 websites where criminals will be able to steal log-ins that control finances. These are the most popular banking sites and online payment services. To expand the number of sites it’s used with, and to ensure that every infected user is at risk, the trojan also monitors a victim’s activity and searches sites visited for keywords like ‘account summary’ or ‘balance’. When it discovers those sites, it alerts it’s host so they can begin attacking those sites as well.
In order to gain access to your computer, hackers first infect websites. When you visit one of these infected websites, vulnerabilities in browser plug-ins are used to install malware directly onto your hard drive. Spam email and links sent over social media are also used to infect users.
To keep your computer, and bank account information safe, don’t follow suspicious looking links and don’t visit untrusted websites. Keep your antivirus program running and up to date, as well.
If you have malware, trojans or viruses on your computer, bring it to Geek Rescue or call us at 918-369-4335. We clean infected machines and help you protect against future attacks.
November 22nd, 2013

Malware for both PCs and smartphones continues to be a growing problem worldwide. Adam Greenberg, of SC Magazine, reports that much of the new malware discovered in the past quarter uses techniques to falsely verify, or by-pass altogether, digital signatures used to validate legitimate applications and files.
Researchers with security company McAfee reported a 30-percent increase in malware for Android,m which equates to about 700-thousand new pieces of malware. Most of this mobile malware is known as “Exploit/MasterKey.A”, which allows for the avoidance of digital signature validation.
This method is also being used in the increasing threat of malware for PCs. Malware for PC users using falsified digital signatures is up 50-percent this quarter with more than 1.5-million new pieces identified.
These latest tactics are more intelligent ways of making users believe a file of application they’ve downloaded is safe for use. Antivirus software company, BitDefender, reported one malware scam that convinces users that they’re downloading an antivirus program called ‘Antivirus Security Pro’. It contains a stolen digital signature and when run, it identifies false examples of malware and demands money to fix the problem.
Examples like this are why it’s important for users to keep security software up to date. Antivirus applications struggle to keep up with the latest tricks of cyber criminals, and it’s impossible for them to catch the latest pieces of malware that attempt to infect your system if they’re out of date.
If your computer or smartphone falls victim to malware, or you’d like to improve your security before the next attack happens, call Geek Rescue at 918-369-4335.
November 21st, 2013

Spam emails began as a nuisance, but one that ultimately wouldn’t harm your computer. Since those early days, spam has evolved to be much more malicious. Now, spam often is the first step to infecting your machine with malware, trojans, keyloggers and viruses. Spam can be used to steal your identity and hold your computer for ransom. Jeff Orloff of The Email Admin posted some threats to be on the look-out for and some tips for how to stay safe.
Cryptolocker is the latest threat making headlines. The trojan is a form of ransomware that first surfaced in August. Most commonly, it stems from an email attachment that infects the victims computer when it’s downloaded. The cryptolocker is then able to encrypt certain types of files on your system and holds them for ransom. To decrypt the data, a payment is required. Often, there is a deadline that goes along with this demand for money. While some users report they’ve paid the ransom and their files were encrypted, others have paid and seen no results. Unfortunately, even professionals struggle to decrypt files that have fallen victim to a cryptolocker.
In less than a week, more than 12-thousand users reported being infected by a cryptolocker in the US. This isn’t the only threat to your security that strikes through email. Cryptolocker is just the latest.
Email security is essential for both your business or your home network. There are a number of options for enhanced email security, but regardless of what you choose, make sure it includes some vital features. Your security software should scan incoming email for known threats and separate those that are potentially harmful. Email protection has to be more intelligent than ever to properly protect you. Spammers are constantly updating their tactics to get around spam filters.
Geek Rescue offers a number of options to keep you safe from the latest cyber threats. Call us at 918-369-4335 to find out how we can protect you.
November 20th, 2013

Stolen smartphones are a big problem in the US. About one in three robberies involves a smartphone and lost or stolen phones total about $30-billion each year, according to the FTC. A possible solution, or at least a tool that could decrease the number of smartphone thefts, has been found, but as Daniel Johnson, of The Telegraph, reports, US carriers have refused to use it.
It’s called ‘Kill Switch’ and it allows phones to be disabled remotely in the event they’re stolen. The thinking is that criminals would be less likely to steal phones if they were immediately disabled and made worthless except for spare parts. Samsung liked the idea so much they began making smartphones with Kill Switch pre-installed. Those phones won’t be available in the US, however.
AT&T, Verizon, T-Mobile and US Cellular have rejected Kill Switch and forced Samsung to remove it from all phones set for distribution in the US. Their official stance is that Kill Switch could be used by hackers to disable phones that haven’t been stolen.
According to some industry insiders, however, the rejection of Kill Switch has more to do with the potential loss of insurance revenue. It’s believed that theft insurance would be less in demand if Kill Switch became standard on all devices. This thinking ignores the fact that insurance would still be useful for lost and broken phones, however.
The problem remains implementing a kill switch in a more secure manner. The possibility of hackers remotely disabling smartphones poses a serious problem, which won’t be easily solved given that Kill Switch is software and software is inherently hackable.
At Geek Rescue, we can’t stop your smartphone from being stolen. But, we can fix nearly any other problem you’re having with your device. For broken or unresponsive screens, slow performance, malware, or any other issue, call us at 918-369-4335 or bring your phone in to one of our locations.
November 15th, 2013

It seems like every week a large-scale password theft makes headlines. The latest was Adobe, who experienced the loss of about 150-million user log-ins. Michael Santarcangelo, of CSO, writes that anytime a large batch of log-in information is stolen it jeopardizes the security of other businesses. There are three steps that should be taken in this event to keep your business secure.
- Check The Email Addresses
When an attack of this nature occurs, the compromised log-in information is made public. If you know where to look, you can look through the list of stolen log-ins for email addresses in your domain. This is important because if an employee had information stolen for one account, it significantly increases the likelihood that their other accounts could be compromised. This could lead an attack to your network. If you see one of your addresses in the list of compromised accounts, be sure to notify the owner of the address, then change their log-in information for your network.
Every password that was stolen is now in a hacker’s database. That means that any individual who uses the same or similar password as a user who had their account compromised is now in danger. Hackers will use these learned passwords to launch more informed, intelligent attacks on accounts. Check your company’s log-ins for similar passwords and get them changed immediately.
Be sure to explain to the affected employees why their account log-ins need to be changed and how a hacker could attack them. Giving them access to better information and training could prevent an attack in the future.
Few business owners understand that the loss of a large group of log-ins and passwords, such as the Adobe situation, could affect them also. Taking these precautions is labor-intensive, but necessary for security.
For help protecting your company from a devastating cyber attack, contact Geek Rescue at 918-369-4335.
November 15th, 2013
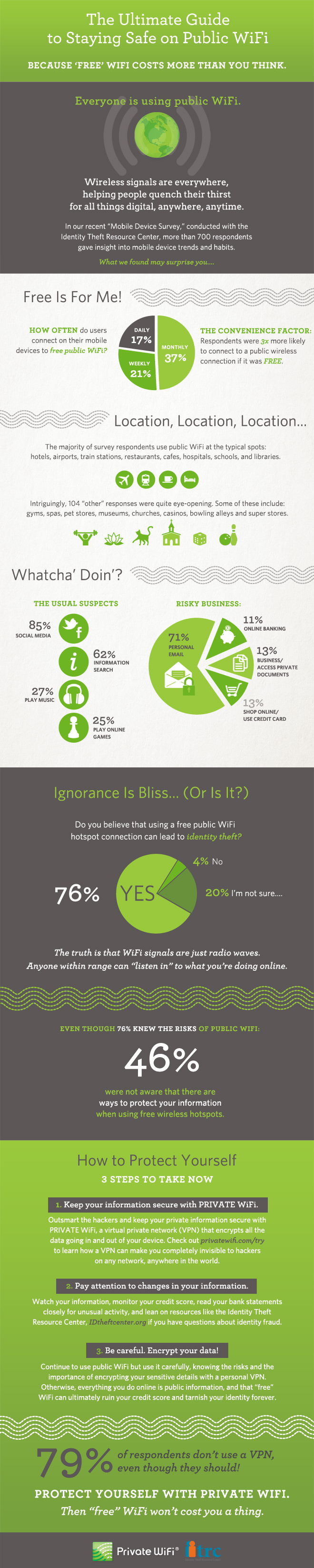
Free, public WiFi is offered nearly everywhere. Whether you’re at a library, coffee shop, restaurant, hotel, airport or hospital, you’ll be able to stay connected. That free WiFi comes with some inherent risks, however. PrivateWiFi and the Identity Theft Resource Center teamed up to produce this infographic, which details the general feelings about free WiFi and how you can stay secure while using it.
More than three-quarters of users understand that public WiFi isn’t secure. That’s the first step in a safer experience because those users will know not to log-in to their personal email or banking site while using an unsecured network. These safe surfing tactics aren’t the only way to improve security, however.
If a public network is unsafe, then why not use a private network? Even when connected to public WiFi, you can use a VPN to immediately improve security. There are a number of VPNs available. While many require a paid subscription, some are free up to a certain point. The VPN encrypts data being sent by your device and the data being returned to it.
A good idea is to keep close tabs on your online accounts, your financial information and your credit score regardless of the kind of network you’ve been using. But, it’s especially important to monitor your information if you know you’ve been on a public network. You probably won’t know immediately if someone hacks into your bank account or steals your identity. Regularly checking this information will save you from devastating damage because you’ll be able to recognize the first signs of trouble.
Understanding what’s at stake and when your information is most vulnerable is an effective way to stay more secure. When using free WiFi, try to avoid any site that require you to log-in. If you absolutely must log-in over an unsecured network, look into putting a VPN in place before doing so.
With more and more free wireless networks available, it’s more important to learn how to safely use them.
For more help improving the security of any of your devices at home or at the office, call Geek Rescue at 918-369-4335.
November 14th, 2013

Spam email is a common problem for anyone with an an email address. Most spam messages are easy to identify, but a practice called brandjacking muddies the distinction between legitimate email and spam. Sue Walsh, of the All Spammed Up blog, reports that a recent brandjacking spam campaign involves Dropbox and attempts to steal banking and credit card information.
This scam starts when an email that appears to be from Dropbox arrives in your inbox. There are multiple variations of the same spam email, but all contain the same basic message. Some, however, are more convincing because they eliminate the typical broken English and poor spelling that marks most spam.
The message informs users that their password is too old and needs to be replaced. Users are then directed to follow the provided link and update their password. This is actually a believable ploy because Dropbox does periodically ask users to change passwords when their account hasn’t been active for an extended period of time.
The link provided doesn’t take users to a Dropbox log-in page, however. Instead, they arrive on a site made to look like it’s owned by Microsoft and told that their browser is out of date. An update is offered up for download, which is actually a Trojan that steals banking and credit card information.
The same group suspected of this scam has brandjacked UPS, Verizon and the Better Business Bureau in the past.
No matter how believable a message is, there are still ways to see through these scams. Before following the instructions of any email, check the sender’s address. In this case, the send won’t have an ‘@dropbox.com’ address, so you can assume the message isn’t legitimate. Also, if you follow a link provided that doesn’t take you where it’s supposed to, it’s another sign that you’re being scammed.
If you have any suspicion that an email you receive from a company isn’t legitimate, contact the company directly by phone.
If your computer has been infected by malware, viruses or Trojans, or you’d like to improve your device’s security before an attack happens, contact Geek Rescue by calling 918-369-4335.




















