September 12th, 2013

Cloud computing has a practically endless list of capabilities, but perhaps the most useful is the cloud’s mobility. Sam Narisi, of IT Manager Daily, published ways your remote workers should use the cloud to increase productivity and collaboration.
If you have remote workers spread across the country, a video conference call introduces unfamiliar faces to each other and brings the team closer together. Even if your employees are all in-house, you may need a conference call with a client, an employee working from home or a team on the road. The cloud makes it easy to connect with anyone, regardless of where they may be. A bonus is that those remote employees will be able to access files and applications needed to enhance their contributions to the conversation.
Sometimes, you need more than a conversation with remote employees or clients. That’s why some cloud based services offer tools like collaborative virtual whiteboards and message boards. This simplifies communication beyond normal email and leaves printed evidence of what’s been said, unlike phone conversations or video conferencing. The whiteboard feature allows users to draw out ideas and other users to add on or erase.
A cloud system is great for off-site back-up and data storage. In the context of mobile access, however, storage refers to the ability of the remote workers to access and collaborate on files stored in the cloud. Documents, spreadsheets and even presentations can be shared between team members and worked on together. Not only does this make the process more efficient, but it ensures that employees will always have access to the files they need, when they need them.
The cloud offers business solutions for nearly every industry. To find out how cloud computing will help your business, contact Geek Rescue at 918-369-4335.
September 12th, 2013

A new form of malware attack on Android phones has security experts on the look-out. This form of scareware infects your computer through a phishing email and malicious link.
Chris Brook, of ThreatPost, reports that the emails will appear to be from the United States Postal Service.
The message informs you that the USPS was unable to deliver your package because the postal code contains an error. You’re then prompted to print a label. When you follow the “Print The Label” link included in the email, a malicious Android Package File, or .apk, is downloaded to your device.
This particular scam seems poorly constructed. After all, most of us know when we’ve sent a package recently and understand that printing a label for a package that isn’t in our possession wouldn’t do much good. However, there are plenty of users who will click the link to try to gain more information, even if they haven’t sent a package in months. Hackers play on our curiosity and even thin attacks like this one will claim victims.
This form of malware has been used before. Security experts note that a previous scam using it in a scam that asks users to pay a subscription fee to keep their devices clear of malware. What’s noteworthy is the way the malware is being distributed. Cyber criminals are adjusting to the number of users who access their email on their Android devices and are attempting to exploit that fact.
This malware is reportedly even capable of intercepting both incoming and outgoing calls. It also is capable of changing file names to look more innocent. Instead of a suspicious .apk file, it will appear as a .zip file with a tantalizing name like vacationphotos.zip.
Android users should go into the settings on their device and disable the option to “allow installation of apps from unknown sources”. Users will also be able to enable a “Verify Apps” option, which will warn them before any potentially malicious app is downloaded.
These two options help keep your device safe, but you’ll also want dedicated security apps as well. To upgrade the security on any of your devices, or to rid them of existing infections, come by or contact Geek Rescue at 918-369-4335.
September 12th, 2013

For users of the web browser Google Chrome, a new malware threat has emerged. This threat looks a lot like Candy Crush and Super Mario.
Eric Johnson, of All Things Digital, describes the “wild west” atmosphere of the Chrome Web App store. Unlike Google Play, the app store for Android mobile devices, Chrome’s Web App store is much less regulated.
This lack of regulation has lead to a number of knock-off apps. Mostly, these apps are recreations of famous games like Super Mario, Candy Crush Saga, Fruit Ninja, Doodle Jump and Sonic the Hedgehog. These games aren’t licensed by their original creators and many are suspected to contain malware.
It’s not hard to understand why malware is included in these recognizable games. Users see a game they played in their youth, or a game they’ve heard is popular now, and want to try it out. It’s a naturally attractive app for what seems like no obligation. However, the apps are usually poor quality and infect your computer with malware.
The key to spotting these knock-off, malicious apps is simple. First, understand that Nintendo, Sega and other giant game companies aren’t making officially licensed apps for Chrome. If you have any further questions, look at the website associated with the app. In the case of a Candy Crush Saga knock-off, the website was listed as candycrushsaga.blogspot.com, which is not associated with King, the game’s developer.
If you have added one of these apps or another app you think contained malware, run your fully updated virus scan after you remove the app from Chrome.
For additional security on any of your devices, contact Geek Rescue at 918-369-4335. We offer security solutions to keep you safe from malware, spam email, viruses and more.
September 11th, 2013

Many small business owners believe that they won’t be the target of a cyber attack simply because there are larger companies that present more value to hackers. However, this belief leads to more relaxed security protocols, which makes small businesses an attractive target because of their ease of access.
Susan Solovic posted on the AT&T Small Business blog how to immediately improve your company’s security without having extensive expertise.
As with any account, you need to protect your business by having each employee log-in with a secure password. This password should be long, have upper and lower case letters and symbols and numbers and be changed often.
It’s a basic step that pays big dividends. Don’t make it easy for a criminal to steal your information or infiltrate your network. When you’re not sitting at your computer, sign out. This erases the possibility that someone in the area could walk by and immediately access valuable data. This is especially important for mobile devices.
There’s a reason your antivirus software requires regular updates. Hackers are constantly changing tactics and using new techniques. Each update is an attempt to stay ahead of the curve. So, when any of your regularly used applications prompts you to update, do it.
Nothing keeps you 100-percent secure. Even if you are able to avoid a cyber attack, natural disasters could still wipe out data. Regularly backing up vital data is important in order to avoid a catastrophe. Should any of your files be lost or corrupted, you’ll have back-ups to replace them quickly without suffering any down time.
Each employee and each position at your company is different. Some will require different access to different applications. Think of it like a government security clearance. There are different levels depending on your pay grade. For your business, give employees the access necessary for them to do their job, but no more. This way, if their account is compromised, you won’t be allowing access to your entire network.
Keeping your business secure is an important and time consuming job. For help, contact Geek Rescue at 918-369-4335. We offer data storage and back-up, security solutions and more.
September 11th, 2013
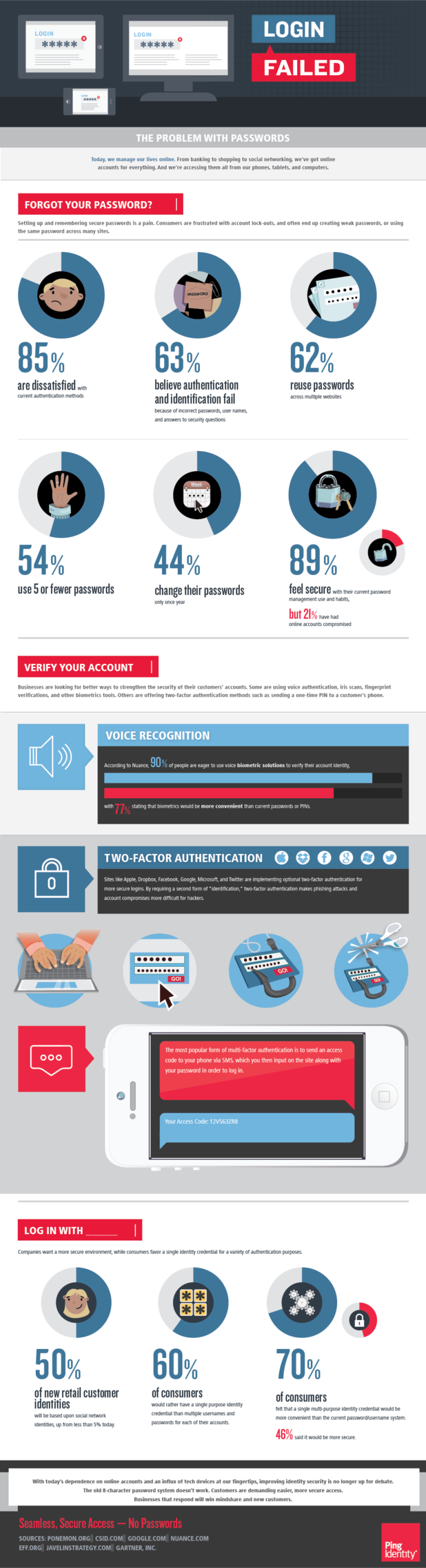
Would you call your passwords to the various accounts you have online secure? It depends on how many characters your password is, if you use upper and lower case letters, symbols and numbers, if you use full words, recognizable names or places from your life and whether you reuse passwords on multiple sites.
Ping Identity’s Christine Bevilacqua published a blog along with the included infographic that speaks to the problem with password security.
Many of us have experienced a compromised online account and a broken password is often to blame. There is software readily available that is capable of breaking even incredibly long passwords. Sometimes, the strength of your password isn’t even the issue.
In the case of the latest attack on the New York Times, a spear phishing scam resulted in an employee giving out their password. Cyber criminals have become increasing intelligent about creating ways to hack into your accounts.
If you aren’t scammed into giving out your password outright, you may be guilty of clicking a link or downloading an attachment you shouldn’t have. This could infect your computer with malware capable of monitoring your activity, stealing passwords and infiltrating your accounts.
Some online accounts are moving to require a log-in with social media accounts, but what protects your social media accounts? A password does.
One of the latest innovations on the new iPhone is the use of biometrics. In order to unlock the phone, users will use their fingerprint. This seems like a foolproof plan. Afterall, no one will be able to hack into your phone unless they have your fingerprint. However, the problem becomes the unreliability of biometrics. For example, what happens if an error occurs and your phone won’t recognize your fingerprint? For most similar systems, the fall back is simple password protection, which brings us back to square one in terms of security.
The key to avoiding a hacker cracking your password is to practice safe surfing techniques and to have the latest security software in place.
To make any of your devices more secure, contact Geek Rescue at 918-369-4335.
September 10th, 2013

It seems like every day there is a new function you are using on your smartphone that you can’t live without. As we use our phones for more and more, our battery dies earlier in the day. But, there are a few simple solutions for making your smartphone’s battery last longer without giving up any of those fancy functions, as suggested on the BeetleBite blog.
If you’re not on the go, or are not currently using a wireless network, there’s no reason to have GPS or WiFi enabled. These features are incredibly useful, but are a strain on your battery. They’re also easy to disable so if you’re concerned about your battery life, they should be the first to go.
Many people leave their phone on vibrate all of the time. This way, there’s no annoying ring tone to worry about and you’re never the person whose phone goes off in the middle of a meeting or movie. When your phone is on vibrate, however, it actually uses quite a bit more of the battery than when you let the ringtone play by itself.
Your display probably eats into your batter more than anything else. This is an unavoidable problem, but you can limit just how draining your display is. Except for a few specific circumstances, you don’t need your screen set to the brightest possible display. By dimming it a few notches, you can gain more battery life.
Surprisingly, the color on your screen’s display makes a difference in how long the battery lasts. Displaying black is less draining than displaying white. So, change your wallpaper to black and your phone could last the whole day.
These tips allow you to use your phone longer before the battery dies and doesn’t demand you give up much functionality.
When your phone needs a fix, for poor performance or for broken hardware, call Geek Rescue at 918-369-4335. If it boots up or turns on, we fix it.
September 10th, 2013

Apple plans to announce their newest models of the iPhone on September 10, which has millions eager to see their newest offering. Among those millions are cyber criminals looking to take advantage of the latest trend.
As Merianne Polintan writes for TrendMicro, phishing emails promising free, new iPhones have already begun to show up in some users inboxes. Most of these early occurrences were spotted in SouthEast Asia, but users in the US should also be on the lookout.
The iPhone phishing email looks like it’s sent to you from the Apple Store. The message tells you that your email has won in a drawing and you’re entitled to a new iPhone 5S. You’re then asked to log in at the link provided to claim your prize.
If you look closely at these emails, you’ll notice the tell-tale signs of a scam. For example, there are a number of spelling or grammatical errors. You’ll also likely find that although the sender is identified as “Apple Store”, the actual email address is probably not “@Apple.com”.
So, unfortunately, you didn’t win a new iPhone. By avoiding this scam, however, you will at least keep your identity from being stolen.
To improve the spam filter on your email or improve the security on any of your devices, contact Geek Rescue at 918-369-4335. We keep you safe from malware, viruses, phishing scams and spam emails.
September 10th, 2013

You’ve no doubt heard the term cloud computing, but did you know now all cloud services are created equal? Infrastructure as a Service, Software as a Service and Platform as a Service all incorporate cloud technology, but offer different advantages.
Gil Allouche, of IT Manager Daily, broke down the difference between these common cloud computing models and explained how businesses use them.
- Infrastructure as a Service
This is almost like outsourcing your IT department. IaaS puts storage, networking and raw computing into the cloud. An outside provider would then manage for running the system and maintenance. Operating systems and applications are then added by your business.
PaaS offers the ability to use operating systems online and rent hardware and storage. Your business is able run applications in the cloud, which makes them accessible by employees from virtually anywhere. Features of operating systems and applications running on PaaS are easily upgraded or altered.
In this model, the cloud provider would manage the software your company needs and you would pay for subscriptions for the number of users you need. With SaaS, the maintenance and installation of software is done for you, which frees up space and time for your own IT infrastructure. Updates are quick and easy and the software is scalable to fit the demands of that moment. An example is Microsoft Office 365. Rather than installing Office 365 on each individual computer at your place of business, you would sign up for SaaS and an outside provider would keep you constantly updated and running smoothly.
As you can see, while there are similarities between cloud models, the services offered are different. Cloud computing is incredibly variable and can be used in an almost endless number of possible ways.
To find out what cloud computing offers your business, contact Geek Rescue at 918-369-4335. We have cloud solutions for every industry and will help you discover how cloud computing makes you more efficient.
September 9th, 2013

If there’s a clicking noise coming from your computer or you encounter a number of freezes, there’s probably a problem with your hard drive. Most manufacturers claim their hard drives last for more than 1-million hours of use, but the failure rate of a drive is about 3 to 5 times higher than that.
A recent post on Techopedia has some tips for how anyone can attempt to fix their hard drive. Before opening up your machine, check your warranties. Many times, trying to fix your own computer will void your warranty, which leaves you no safety net if you aren’t successful.
There are paid services and free services to back-up the data on your hard drive. The important thing is to make sure you have a back-up in case your drive completely fails. This is good advice whether your hard drive is acting up or not.
More recent versions of Windows is actually capable of fixing some of the minor errors on your hard drive. Right click the your hard drive in the “My Computer” menu, go to “Properties”, then “Tools” and select “Check Now”.
If the “Check Now” tool crashes, there’s a serious problem with your hard drive. Even if it runs successfully, it may tell you you’re due for a replacement. Before replacing it, however, deactivate software like Office 365. This way, you can restore from back-up on your new hard drive.
There are programs available that will clone your hard drive, which then allows you to put the cloned drive onto a new, healthy hard drive. This way, you won’t be starting from scratch and you’ll be sure all your data and programs are already in place. If the errors on your old hard drive are from viruses, however, you’ll just be infecting the new drive as well. So use caution with this option.
Your hard drive is arguably the most important piece of your computer. If it isn’t working properly, your entire computer can be virtually useless. While there are some easy fixes for common problems, some issues are best left to the professionals.
If your computer isn’t working properly, bring it to Geek Rescue. Our staff will diagnose and fix the problem quickly and efficiently. We work on a variety of devices so if it boots up or turns on, we fix it. Come by or call us at 918-369-4335.
September 9th, 2013

You’ve probably heard of phishing and even spear phishing. But have you heard of smishing?
Criminals are using text messages, or SMS, to send phishing scams directly to your smartphone. Dubbed smishing by some, it’s another way for hackers to steal your money, information or monitor your activity.
Just like phishing and spear phishing, smishing relies on social engineering to play on your fears. Most smishing messages offer you money or gift cards, or claim to be your bank or credit card company.
About.com’s Andy O’Donnell published some tips to help you avoid becoming a victim of a smishing scam.
- Know Your Bank’s Texting Policy
If your bank sends you a text regularly, it might be harder to decide when it isn’t legitimate. However, if you’ve never received a text from your bank before, you should be extremely wary when a text from a bank shows up on your phone. This goes for any accounts you have with any company. If a text comes to you, don’t respond to it. Instead, look up the customer service number for that business and contact them directly.
When an email-to-text service is used, a 4-digit number will usually be shown as the sender. Not all email-to-text users are malicious, but criminals use them to mask their actual location. If you get a text from someone without a typical phone number, be extra cautious.
- Use The Text Alias Feature
If you seem to be getting a lot of spam texts, or just don’t want to worry about them, your phone provider likely offers a text alias feature. This allows you to use an alias number to send and receive text messages and you can then block texts from coming to your actual number. This alias will only be known to those you give it out to, so scammers won’t have access to it.
As mentioned earlier, email-to text and other internet text relay services help scammers mask their identity and allows them to send a high volume of messages. Your cell phone provider will allow you to block all texts coming from these services. This will reduce the number of smishing texts you receive, but you might also miss out on legitimate texts from companies using these services.
Putting additional security on your mobile device is another great way to ensure your safety. To find out more about mobile security, contact Geek Rescue at 918-369-4335.




















